**加密解密基础、PKI及SSL、创建私有CA**
2017-09-14 18:43
435 查看
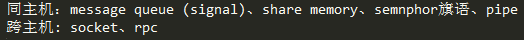
进程间通信
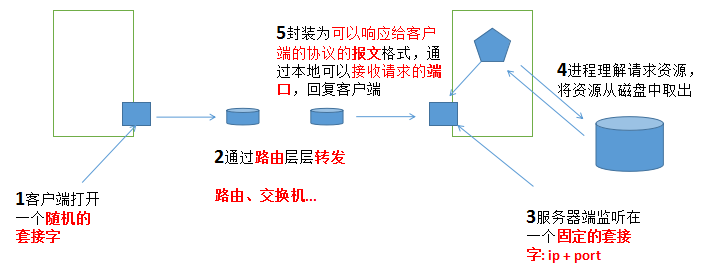
socket通信
客户端-->请求--> 路由转发 --> 服务端,取出资源 --> 封装为可响应给客户端的请求报文从接收请求端口发出
SSL/TLS协议的实现 OpenSSL
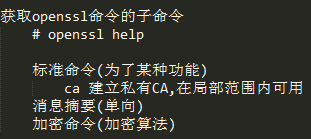
OpenSSL程序组件
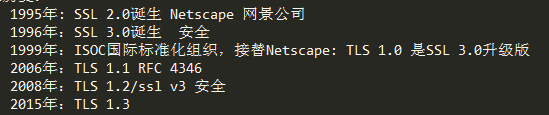
SSL Secure Socket Layer 安全的套接字层
TLS Transfer Layer Secure 传输层安全
SSL分层
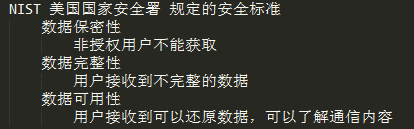
NIST制定的安全标准:保密性、完整性、可用性
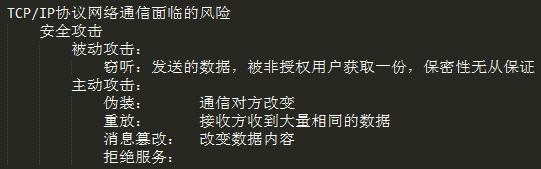
SOCKET通信模型中面临的风险:窃听、伪装、重放、消息篡改、拒绝服务
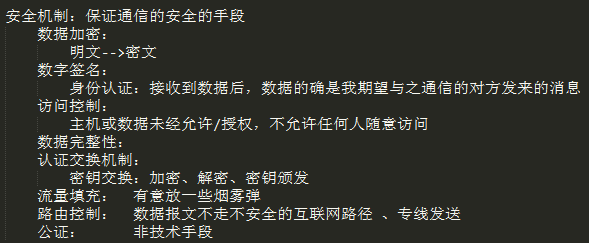
保证安全的手段(安全机制):加密、身份认证、访问控制、完整性校验、路由控制、公证
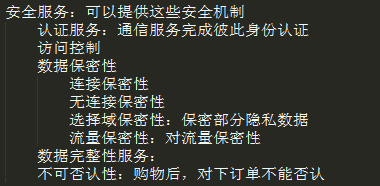
提供安全机制的服务:认证、访问控制、保密性、完整性、不可否认性
保证服务的安全(算法和协议):对称、非对称、单向、密钥交换
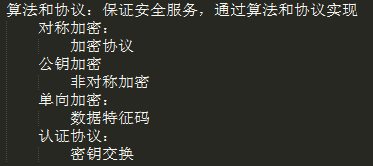
加密解密的基础原理
对称加密、非对称加密、单向加密、密钥交换

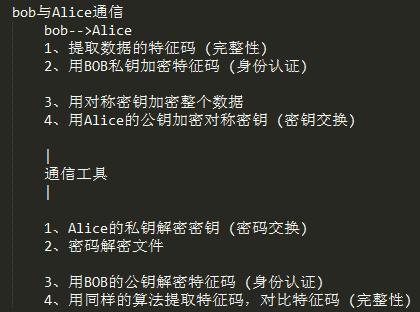
[b]证书颁发机构CA、证书的作用[/b]
[b]
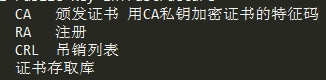
[/b]
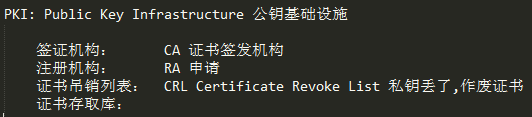
[b]PKI
[/b]
[b]
[/b]
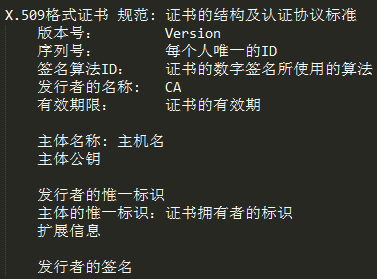
[b]证书的规范
[/b]
[b]
[/b]
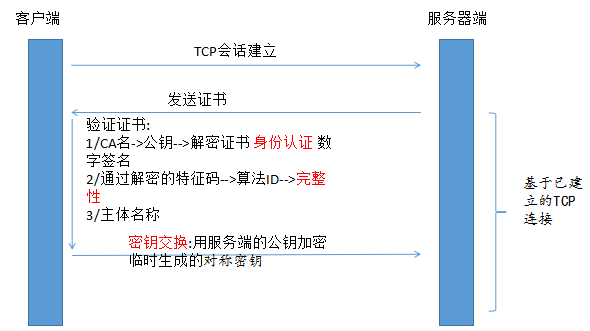
[b]基于公钥加密通信机制[/b]
[b]SSL Hand shark[/b][b]: 一个IP地址只能建立一个SSL会话[/b]
[b]
[/b]
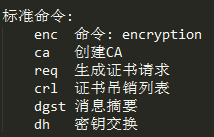
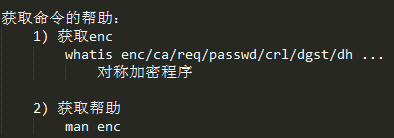
openssl工具使用
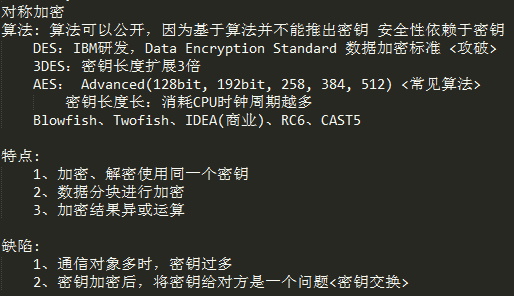
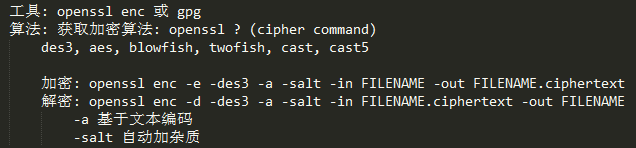
对称加密
使用示例
使用示例
生成用户密码
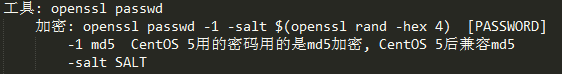
使用示例
生成随机数
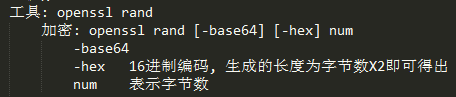
使用示例
生成密钥对
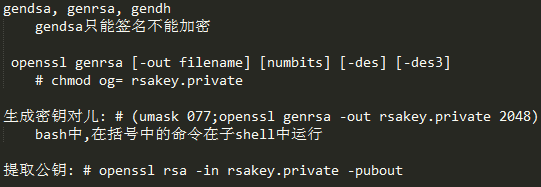
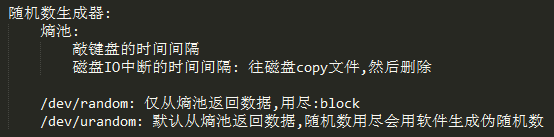
使用示例
# openssl genrsa -out lcc.private 1024
# openssl rsa -in lcc.private -out lcc.pubkey -pubout
私有网络安全通信的实现方案
构建私有CA
传给CA
CA所在的主机必须有软件能得以实现SSH协议<dropbear, telnet, openssh-server>,才能使用客户端工具<scp, sftp, ssh>
CA验证
CA签发
从证书存取库中获取证书
验证证书
在客户端进行吊销证书
1、获取serial
2、在CA,index.txt中查看serial与客户端是否相同
吊销
3、生成吊销证书编号
4、更新吊销列表
5、查看crl文件

socket通信
客户端-->请求--> 路由转发 --> 服务端,取出资源 --> 封装为可响应给客户端的请求报文从接收请求端口发出


SSL/TLS协议的实现 OpenSSL
OpenSSL程序组件
[root@localhost CA]# rpm -ql openssl /usr/lib/libcrypto.so.10 //加密解密库 (C,C++程序员调用的库) /usr/lib/libssl.so.10 //ssl/tls实现 (C,C++程序员调用的库) HTTP --> HTTPS /usr/bin/openssl //命令行工具
SSL Secure Socket Layer 安全的套接字层
TLS Transfer Layer Secure 传输层安全

SSL分层
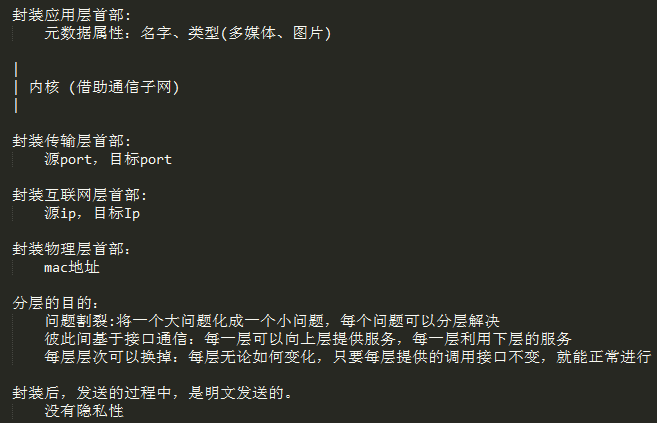
用组件拼装而成的密码学协议软件(TLS, SSL) 标准算法组合成半成品 算法实现:AES-128-CBC-PKCS7 算法原语:AES(对称加密),RSA(非对称加密),MD5(单向加密)
NIST制定的安全标准:保密性、完整性、可用性
SOCKET通信模型中面临的风险:窃听、伪装、重放、消息篡改、拒绝服务
保证安全的手段(安全机制):加密、身份认证、访问控制、完整性校验、路由控制、公证
提供安全机制的服务:认证、访问控制、保密性、完整性、不可否认性
保证服务的安全(算法和协议):对称、非对称、单向、密钥交换





加密解密的基础原理
对称加密、非对称加密、单向加密、密钥交换





[b]证书颁发机构CA、证书的作用[/b]
[b]

[/b]
[b]PKI
[/b]
[b]

[/b]
[b]证书的规范
[/b]
[b]

[/b]
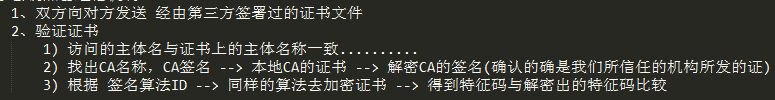
# openssl x509 -in /etc/pki/CA/certs/httpd.crt -noout -text -subject -serial Certificate: Data: Version: 3 (0x2) //版本号 Serial Number: 1 (0x1) //序列号(每个从的惟一标识) Signature Algorithm: sha1WithRSAEncryption //签名算法ID Issuer: C=CD, ST=CD, L=ChengDu //CA名称 //证书有效期 Not Before: Sep 21 07:16:20 2017 GMT Not After : Sep 21 07:16:20 2018 GMT Subject: C=CD, ST=CD, O=MageEdu, //主体名称(主机名) Subject Public Key Info: //主体公钥 Modulus: 00:eb:bd:58:2d:05:54:49:6d:ac:42:98:ee:cb:fb: ec:62:20:e1:1e:e4:64:ef:a3:0f:23:17:5b:fb:66: 6d:a9:ce:81:c3:53:b5:f8:d9:87:da:c5:f3:2d:77: f2:de:3b:ed:92:81:a5:6c:73:f6:83:3c:c2:e5:71: 49:02:02:ae:45:d0:e0:45:f2:41:34:f8:25:87:41: 82:aa:27:e2:17:ca:fc:74:f3:50:98:b0:6c:b0:26: 8b:a5:0d:a7:ca:4b:f5:72:f9:44:87:8b:15:51:ea: 9a:84:6d:22:aa:fe:84:62:5a:59:33:c3:ff:29:51: a9:1a:56:c3:63:22:9a:6d:2c:65:10:a0:57:78:c2: aa:70:3d:32:eb:59:dc:f7:a9:0c:ea:e5:8e:29:1c: 2f:27:0d:53:87:e1:2b:eb:fe:f8:8f:61:8f:86:ab: f1:9c:ee:29:11:c1:71:ca:41:24:3e:1d:e1:3c:84: 60:8a:d8:4d:ad:4c:b2:ca:8f:25:29:8a:11:1a:6f: 1c:03:88:4a:66:99:73:34:7d:76:da:85:77:da:65: 3a:e5:d3:ca:58:9f:8c:3a:3b:d5:e2:9e:77:1e:b2: f3:c8:5a:b6:2d:2b:68:71:20:9f:94:41:0c:4b:2f: 93:f5:11:4c:89:9e:d9:48:ac:de:62:d9:5e:16:73: 5d:39 Exponent: 65537 (0x10001) X509v3 extensions: //扩展信息 X509v3 Subject Key Identifier: //发行者的惟一标识 C5:AE:93:32:58:BC:DC:F4:97:E5:D7:52:15:37:11:4D:ED:4C:B1:8E X509v3 Authority Key Identifier: //主体的惟一标识 keyid:D4:F7:60:6F:E8:F4:2D:A6:F7:5D:09:55:D2:5D:56:DE:1F:93:91:33 Signature Algorithm: sha1WithRSAEncryption //发行者签名,签名算法 3c:90:f8:cf:d6:91:36:ab:4b:12:27:22:78:85:7f:32:15:4e: ac:60:30:63:65:fe:91:be:1b:e5:22:65:34:4d:f0:b2:2c:d9: 43:38:b9:76:1e:10:ca:27:ab:e9:db:00:bd:d9:87:96:b5:a9: ee:34:34:01:05:88:fc:59:ef:1d:9b:3f:8e:49:fa:e8:c9:54: 15:d0:63:14:7d:51:e9:c8:8c:50:77:81:5c:f2:56:f8:c2:ba: 16:46:cc:7f:e2:72:27:56:4e:a7:c4:2c:b4:64:44:9a:84:bc: b2:19:5e:dd:3c:20:1c:a9:8c:93:ae:94:e4:8d:8e:d1:b7:47: 3a:c5:f6:df:42:6f:d9:66:d8:25:97:03:94:01:60:f5:a7:60: c3:33:55:c3:cb:12:f8:14:1e:df:17:00:26:49:ce:74:fc:8f: 56:16:10:b3:16:6e:09:06:8c:8f:84:e9:ec:e2:84:06:82:ac: 27:8d:c5:f6:83:d8:3d:8d:de:d9:3e:e7:ae:15:41:a9:8d:42: e9:9d:8d:b8:d7:29:47:21:45:3c:39:49:7a:96:31:bb:95:93: 7b:1b:29:07:dc:fe:ad:7c:f0:28:c5:cb:b5:65:8f:1f:7e:60: a3:86:50:9f:c3:da:53:1f:6b:ec:ab:7c:1a:7e:39:40:37:23: 83:17:39:54 subject= /C=CD/ST=CD/O=MageEdu/OU=Ops/CN=www.magedu.com/emailAddress=lccnx.foxmail.com serial=01 1、找到CA名,和签名算法 2、找到信任机构的CA证书 3、用证书中的公钥解密加密的数字签名 //身份认证 4、用相同的签名算法对证书提取特征码 //完整性检验 5、比对特征码是否相同
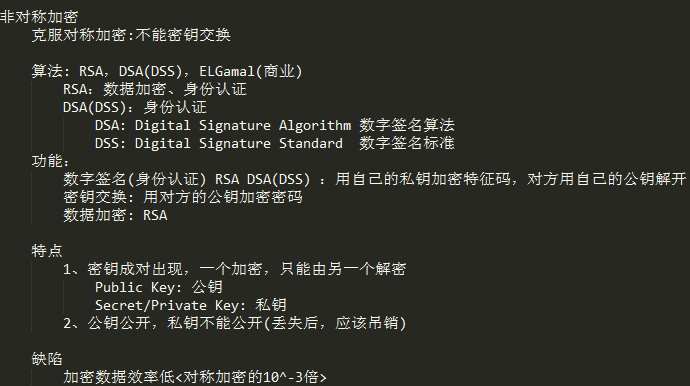
[b]基于公钥加密通信机制[/b]

[b]SSL Hand shark[/b][b]: 一个IP地址只能建立一个SSL会话[/b]
[b]

[/b]
openssl工具使用




对称加密

使用示例
使用示例: 1、创建临时文件 # mktemp -p /tmp lcc.XXXX /tmp/lcc.hFdo 2、加密 # openssl enc -e -seed-cfb -a -salt -in lcc.hFdo -out lcc.ciphertext 3、解密 # openssl enc -d -seed-cfb -a -salt -in lcc.ciphertext -out lcc.txt单向加密

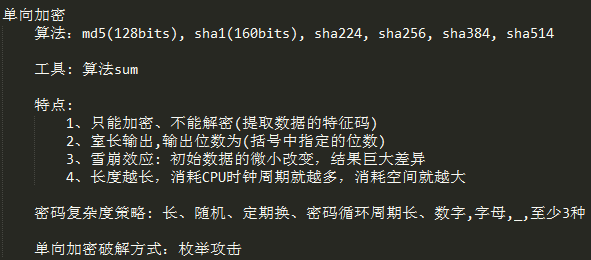
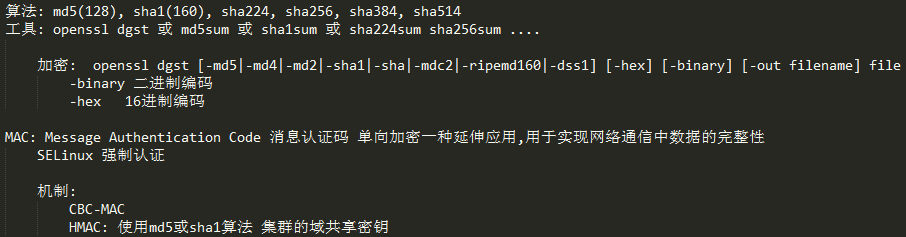
使用示例
# sha1sum lcc.txt 5448d7dc19288c6ee87a25d4e2e990f72d786971 lcc.txt # openssl dgst -sha1 -hex lcc.txt SHA1(lcc.txt)= 5448d7dc19288c6ee87a25d4e2e990f72d786971
生成用户密码

使用示例
# openssl passwd -1 -salt $(openssl rand -hex 4) # openssl passwd -1 -salt $(openssl rand -hex 4) 123
生成随机数

使用示例
# openssl rand -hex 4 (8位) # openssl rand -base64 16 | tr -d '='
生成密钥对


使用示例
# openssl genrsa -out lcc.private 1024
# openssl rsa -in lcc.private -out lcc.pubkey -pubout
私有网络安全通信的实现方案
构建私有CA
# echo "01" > /etc/pki/CA/serial //必须为01,否则签发不了 # touch /etc/pki/CA/index.txt # cd /etc/pki/CA # (umask 077;openssl genrsa -out private/cakey.pem 1024) # openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 7300申请请求
# install -d /etc/httpd/ssl # cd /etc/httpd/ssl # (umask 077;openssl genrsa -out httpd.key 1024) # openssl req -new -key httpd.key -out httpd.csr -days 365
传给CA
CA所在的主机必须有软件能得以实现SSH协议<dropbear, telnet, openssh-server>,才能使用客户端工具<scp, sftp, ssh>
# scp -P 9999 /etc/httpd/ssl/httpd.csr root@192.168.80.129
CA验证
CA签发
# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt -days 365
从证书存取库中获取证书
# scp -P 9999 root@192.168.80.129:/etc/pki/CA/certs/httpd.crt /etc/httpd/ssl/
验证证书
# openssl x509 -in certs/httpd.crt -noout -serial -subject serial=01 subject= /C=CD/ST=CD/O=MageEdu/OU=Ops/CN=www.magedu.com/emailAddress=lccnx.foxmail.com
在客户端进行吊销证书
1、获取serial
# openssl x509 -in /etc/httpd/ssl/httpd.crt -noout -serial -subject
2、在CA,index.txt中查看serial与客户端是否相同
吊销
# openssl ca -revoke newcerts/01.pem Using configuration from /etc/pki/tls/openssl.cnf Revoking Certificate 01. Data Base Updated
3、生成吊销证书编号
# echo "01" > /etc/pki/CA/crlnumber
4、更新吊销列表
# openssl ca -gencrl -out thisca.crl Using configuration from /etc/pki/tls/openssl.cnf
5、查看crl文件
# openssl crl -in thisca.crl -noout -text Certificate Revocation List (CRL): Version 2 (0x1) //版本号 Signature Algorithm: sha1WithRSAEncryption //签名算法 Issuer: /C=CD/ST=CD/L=ChengDu/O=MageEdu/OU=Ops/CN=ca.magedu.com/emailAddress=lccnx@foxmail.com Last Update: Sep 21 08:14:35 2017 GMT 有效期 Next Update: Oct 21 08:14:35 2017 GMT CRL extensions: 扩展信息 X509v3 CRL Number: 吊销号码 1 Revoked Certificates: Serial Number: 01 Revocation Date: Sep 21 08:12:49 2017 GMT Signature Algorithm: sha1WithRSAEncryption 5d:9e:a2:60:e3:78:9d:24:42:92:b6:72:81:92:43:d7:02:12: 54:f0:8e:08:21:d8:55:34:1c:70:53:8d:ac:bd:44:15:37:30: ba:ef:d2:79:24:52:83:a1:bb:39:70:af:93:10:64:06:b6:e6: 76:fd:12:cf:b5:f7:07:16:c6:cd:08:a9:46:d3:76:64:24:93: 7d:b4:5a:6d:da:38:08:31:7b:6e:76:a6:4e:5a:c2:cc:e6:24: be:76:b9:38:46:ed:c7:16:61:88:8c:ac:90:bd:4e:c9:9d:e5: 73:8a:76:c4:57:82:80:29:06:c8:81:cd:7b:37:08:ee:81:25: d6:04:8e:dd:dd:d8:1b:47:44:e4:bb:bc:3c:7f:cb:97:68:27: b0:32:ea:fb:d1:84:91:7e:50:05:14:0a:1d:65:2a:5e:ba:41: 1d:dd:a4:39:e5:d2:b5:2b:33:b0:56:b3:78:cc:99:69:c9:89: 0e:a0:71:f1:5f:ca:40:57:73:72:4d:f0:3d:ea:57:d7:53:6d: 90:ca:59:57:65:1b:ec:b5:4d:6f:7e:41:64:c1:c6:d4:ab:b1: 01:b5:a3:e3:67:0c:59:c9:bc:e6:6c:d1:ae:20:05:3f:85:87: 32:f8:bf:3c:9a:ba:e8:c2:e9:fd:e8:b8:54:92:86:45:95:ca: c3:53:13:41
相关文章推荐
- linux加密解密基础、PKI及SSL、创建私有CA
- 加密解密基础、PKI及SSL、创建私有CA
- 加密解密基础、PKI及SSL、创建私有CA
- 加密解密基础、PKI及SSL、创建私有CA
- 加密解密基础、PKI及SSL、创建私有CA
- 加密和解密技术基础、PKI及创建私有CA
- PKI SSL CA 加密解密基础
- Linux学习笔记之 加密解密介绍,以及运用Openssl创建私有CA
- 加密解密、openssl、私有CA创建过程
- 我的学习笔记1:加密、解密,以及OpenSSL创建私有CA
- 加密解密技术基础、PKI及创建私有CA
- 以PKI为基础的CA工作原理及 加密、解密过程
- 加密解密技术基础、PKI及创建私有CA
- 加密解密技术基础、PKI、及创建私有CA
- 加密和解密基础知识、linux上的私有CA实现方法、学习总结
- 加密解密技术基础、PKI及创建私有CA
- 加密解密技术基础、PKI及创建私有CA
- 网络通信中的加密解密及openssl和创建私有CA详解
- 加密解密基础及openssl构建私有CA初步
- 加密、解密的原理及Openssl创建CA和ssh的基础应用
