linux命令:DNS域名解析,bind
2017-01-09 10:45
260 查看
DNS:Domain Name Service 域名服务
DNS服务器的软件bind:berkeley internet name domain
named-checkconf:检查配置文件是否有语法错误命令
named-checkzone:检查区域文件是否有语法错误命令
dig:domain information groper
dig -t NS . 查找根域的所有DNS服务器
bind97:
/etc/named.conf 主配置文件
BIND进程的工作属性
区域的定义
/etc/rndc.key
rndc: Remote Name Domain Controller
密钥文件
配置信息:/etc/rndc.conf
/var/named/ 区域数据文件
/etc/rc.d/init.d/named {start|stop|restart|status|reload}
二进制程序:named
bind-chroot:
默认:named
用户:named
组:named
/var/named/chroot/
etc/named.conf
etc/rdnc.key
sbin/named
var/named/
[root@test ~]# yum list all |grep bind
This system is not registered with RHN.
RHN support will be disabled.
bind-libs.i386 30:9.3.6-4.P1.el5 installed
bind-utils.i386 30:9.3.6-4.P1.el5 installed
[root@test ~]# rpm -e bind-libs bind-utils #rpm -e 卸载软件包
[root@test ~]# yum list all |grep bind
This system is not registered with RHN.
RHN support will be disabled.
bind.i386 30:9.3.6-4.P1.el5 Media
bind-chroot.i386 30:9.3.6-4.P1.el5 Media
实验环境:CentOS6.5
一、bind安装
bind98下载地址:http://mirrors.ctyun.cn/centos/5/os/i386/CentOS/[root@johntest ~]# rpm -ivh bind97-libs-9.8.0-21.P2.el5.i386.rpm
warning: bind98-libs-9.8.0-21.P2.el5.i386.rpm: Header V3 DSA signature: NOKEY, key ID e8562897
Preparing... ################################### [100%]
1:bind98-libs ################################# [100%][root@johntest ~]# bind98-utils-9.8.0-21.P2.el5.i386.rpm
warning: bind98-utils-9.8.0-21.P2.el5.i386.rpm: Header V3 DSA signature: NOKEY, key ID e8562897
Preparing... ############################## [100%]
1:bind98-utils ############################ [100%]
[root@johntest ~]# rpm -ivh bind98-9.8.0-21.P2.el5.x86_64.rpm
warning: bind98-9.8.0-21.P2.el5.x86_64.rpm: Header V3 DSA signature: NOKEY, key ID e8562897
Preparing... ########################################### [100%]
1:bind97 ########################################### [100%]
二、编辑DNS主配置文件:
vim /etc/named.conf修改主配置文件,如下图:修改三个红色地方,保存退出
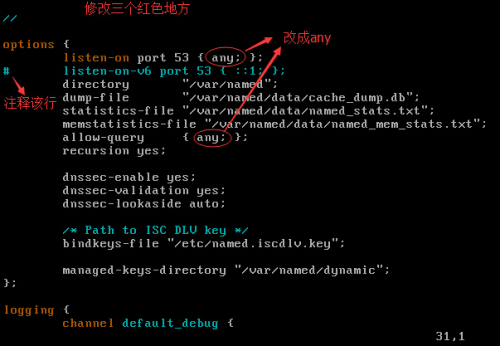
接着修改named.rfc1912.zones文件,vim /etc/named.rfc1912.zones,如下图:
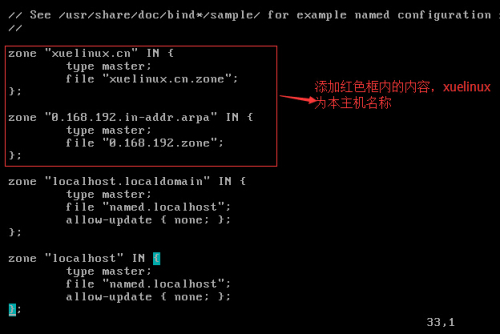
三、添加设置DNS正向解析 修改zone配置文件,正向解析:[root@xuelinux etc]#cd /var/named/[root@xuelinux etc]#cp named.localhost xuelinux.cn.zone #复制并改名修改里面的内容[root@xuelinux etc]#vim xuelinux.cn.zone #("xuelinux.cn.zone"名称要和主配置文件[/etc/named.rfc1912.zones]里面定义的zone文件名一致)
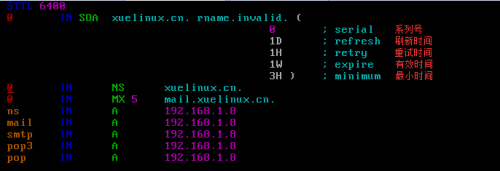
5、修改zone配置文件,反向解析:[root@xuelinux etc]#cd /var/named/[root@xuelinux named]#cp named.localhost 1.168.192.zone[root@xuelinux named]#vim 1.168.192.zone(1.168.192.zone名称要和主配置[/etc/named.rfc1912.zones]文件里面定义的zone文件名一致)
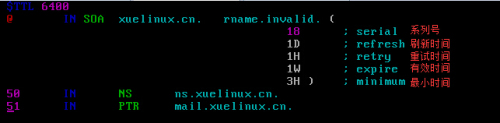
6、更改防火墙设置和selinux设置[root@xuelinux named]#getenforce #查看selinux是否开启setenforce 0[root@xuelinux named]#vi /etc/sysconfig/iptables #配置防火墙端口-AINPUT -m state --state NEW -m tcp -p tcp --dport 53 -j ACCEPT-AINPUT -m state --state NEW -m udp -p udp --dport 53 -j ACCEPT-AINPUT -m state --state NEW -m tcp -p tcp --dport 953 -j ACCEPT[root@xuelinux named]#service iptables restart #重启防火墙,使规则生效
7、启动DNS服(注意DNS服务名称在linux是叫做bind)[root@xuelinux named]#service named start #启动DNS服务
8、测试检测域信息是否正常(重要)检查之前先看下 配置文件有没有读取权限 ll /var/named (如果没有读取权限, chmod +r /var/named/* 即可)

9、检查bind文件配置过程中容易出错以下命令用以检查bind配置文件及zone文件语法是否错误[root@xuelinux named]#named-checkconf /etc/named.conf[root@xuelinux named]#named-checkzone xuelinux.cn /var/named/ xuelinux.cn.zone
10、启动重启DNS服务,查看服务状态[root@xuelinux named]#service named restart[root@xuelinux named]#service network restart
测试:
通过其他PC用户端测试解析,通过nslookup进行测试,
登录到192.168.1.10客户端进行如下测试:

五、更改配制文件后即可限定查询段[root@xuelinux etc]# vi named.conf
options {
directory "/var/named"; allow-recursion { 192.168.1.0/24; }; //只允许此IP段递归查询
};zone "." IN {
type hint;
file "named.ca";
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-transfer { none; }; //none不允许所有客户端发出传送请求
};
zone "0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-transfer { none; };
};
zone "jacktest.com" IN {
type master;
file "jacktest.com.zone";
allow-transfer { 192.168.1.5; }; //只允许此IP发出传送请求
};
zone "1.168.192.in-addr.arpa" IN {
type master;
file "192.168.1.zone";
allow-transfer { 192.168.1.5; };
};[root@johntest etc]# tail /var/log/messagesDec 15 14:11:41 test named[7276]: zone 1.168.192.in-addr.arpa/IN: loaded serial 2016121401
Dec 15 14:11:41 test named[7276]: zone jacktest.com/IN: loaded serial 20161214
Dec 15 14:11:41 test named[7276]: zone localhost/IN: loaded serial 0
Dec 15 14:11:41 test named[7276]: running
Dec 15 14:13:31 test named[7276]: client 192.168.1.5#58423: transfer of 'jacktest.com/IN': AXFR started
Dec 15 14:13:31 test named[7276]: client 192.168.1.5#58423: transfer of 'jacktest.com/IN': AXFR ended
六、设置从DNS服务器
[root@jacktest named]# setenforce 0
setenforce: SELinux is disabled[root@jacktest named]# scp 192.168.1.3:/etc/named.conf /etc/
The authenticity of host '192.168.1.3 (192.168.1.3)' can't be established.
RSA key fingerprint is c2:f2:75:5c:ab:4a:43:d3:e1:76:bc:d2:0f:c7:d6:32.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.1.3' (RSA) to the list of known hosts.
root@192.168.1.3's password:
named.conf
[root@johntest etc]# vi /etc/named.conf...
zone "jacktest.com" IN {
type slave;
file "slaves/jacktest.com.zone";
allow-transfer { 192.168.1.5; };
};
zone "1.168.192.in-addr.arpa" IN {
type slave;
file "slaves/192.168.1.zone";
allow-transfer { 192.168.1.5; };
};验证:
[root@johntest slaves]# tail /var/log/messages #192.168.1.3主
Dec 15 15:43:35 test named[7595]: zone 1.168.192.in-addr.arpa/IN: loaded serial 2016121401
Dec 15 15:43:35 test named[7595]: zone jacktest.com/IN: loaded serial 20161214
Dec 15 15:43:35 test named[7595]: zone localhost/IN: loaded serial 0
Dec 15 15:43:35 test named[7595]: running
Dec 15 15:44:12 test named[7595]: client 192.168.1.5#47432: transfer of 'jacktest.com/IN': AXFR started
Dec 15 15:44:12 test named[7595]: client 192.168.1.5#47432: transfer of 'jacktest.com/IN': AXFR ended
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#34268: transfer of 'jacktest.com/IN': AXFR started
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#34268: transfer of 'jacktest.com/IN': AXFR ended
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#59389: transfer of '1.168.192.in-addr.arpa/IN': AXFR started #传送开始
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#59389: transfer of '1.168.192.in-addr.arpa/IN': AXFR ended #传送结果[root@johntest named]# tail /var/log/messages #192.168.1.5
Dec 15 17:28:13 jacktest named[10089]: zone localhost/IN: loaded serial 0
Dec 15 17:28:13 jacktest named[10089]: running
Dec 15 17:28:13 jacktest named[10089]: zone jacktest.com/IN: Transfer started.
Dec 15 17:28:13 jacktest named[10089]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: connected using 192.168.1.5#34268
Dec 15 17:28:13 jacktest named[10089]: zone jacktest.com/IN: transferred serial 20161214
Dec 15 17:28:13 jacktest named[10089]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: Transfer completed: 1 messages, 9 records, 233 bytes, 0.004 secs (58250 bytes/sec)
Dec 15 17:28:13 jacktest named[10089]: zone 1.168.192.in-addr.arpa/IN: Transfer started.
Dec 15 17:28:13 jacktest named[10089]: transfer of '1.168.192.in-addr.arpa/IN' from 192.168.1.3#53: connected using 192.168.1.5#59389
Dec 15 17:28:13 jacktest named[10089]: zone 1.168.192.in-addr.arpa/IN: transferred serial 2016121401
Dec 15 17:28:13 jacktest named[10089]: transfer of '1.168.192.in-addr.arpa/IN' from 192.168.1.3#53: Transfer completed: 1 messages, 7 records, 219 bytes, 0.002 secs (109500 bytes/sec)
七、测试NS自动更新到从服务器
[root@johntest named]# vi jacktest.com.zone #192.168.1.3主
$TTL 600
jacktest.com. IN SOA ns1.jacktest.com. admin.jacktest.com. (
2016121404 #3改成4
...
imap IN A 192.168.1.6haha IN A 192.168.1.7 #新增一条记录
[root@test named]# service named reload
Reloading named: [ OK ]
[root@johntest named]# tail /var/log/messages #192.168.1.3主NS
Dec 16 10:05:53 test named[10112]: reloading configuration succeeded
Dec 16 10:05:53 test named[10112]: reloading zones succeeded
Dec 16 10:05:53 test named[10112]: zone jacktest.com/IN: loaded serial 2016121404
Dec 16 10:05:53 test named[10112]: zone jacktest.com/IN: sending notifies (serial 2016121404)
Dec 16 10:05:53 test named[10112]: client 192.168.1.5#50038: transfer of 'jacktest.com/IN': AXFR-style IXFR started
Dec 16 10:05:53 test named[10112]: client 192.168.1.5#50038: transfer of 'jacktest.com/IN': AXFR-style IXFR ended
[root@johntest named]# tail /var/log/messages #192.168.1.5从NS
Dec 16 10:08:38 jacktest named[12536]: client 192.168.1.3#6791: received notify for zone 'jacktest.com'
Dec 16 10:08:38 jacktest named[12536]: zone jacktest.com/IN: Transfer started.
Dec 16 10:08:38 jacktest named[12536]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: connected using 192.168.1.5#50038
Dec 16 10:08:38 jacktest named[12536]: zone jacktest.com/IN: transferred serial 2016121404
Dec 16 10:08:38 jacktest named[12536]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: Transfer completed: 1 messages, 13 records, 309 bytes, 0.002 secs (154500 bytes/sec)
Dec 16 10:08:38 jacktest named[12536]: zone jacktest.com/IN: sending notifies (serial 2016121404)[root@johntest slaves]# cat jacktest.com.zone #192.168.1.5从NS
jacktest.com IN SOA ns1.jacktest.com. admin.jacktest.com. (
2016121404 ; serial
...
ftp CNAME www
haha A 192.168.1.7 #自动学习成功
八、开放[b]远程访问DC[/b]Remote Name Daemon Control # [di:mn]守护进程
[root@johntest ~]# rndc-confgen > /etc/rndc.conf
[root@johntest ~]# cat /etc/rndc.conf
# Start of rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "PElKGniJbHk/esQ9zpN+xg==";
};
options {
default-key "rndc-key";
default-server 127.0.0.1;
default-port 953;
};
# End of rndc.conf
# Use with the following in named.conf, adjusting the allow list as needed:
# key "rndc-key" {
# algorithm hmac-md5;
# secret "PElKGniJbHk/esQ9zpN+xg==";
# };
#
# controls {
# inet 127.0.0.1 port 953
# allow { 127.0.0.1; } keys { "rndc-key"; };
# };
# End of named.conf #绿色部分复制添加到named.conf
[root@johntest ~]# rndc -c /etc/rndc.conf status
rndc: connection to remote host closed
This may indicate that
* the remote server is using an older version of the command protocol,
* this host is not authorized to connect,
* the clocks are not synchronized, or
* the key is invalid.
[root@johntest ~]# rm /etc/rndc.key
rm: remove regular file `/etc/rndc.key'? y
[root@test ~]# rndc -c /etc/rndc.conf status
rndc: connection to remote host closed
This may indicate that
* the remote server is using an older version of the command protocol,
* this host is not authorized to connect,
* the clocks are not synchronized, or
* the key is invalid.
[root@test ~]# service named restart
Stopping named: . [ OK ]
Generating /etc/rndc.key: [ OK ]
Starting named: [ OK ]
[root@johntest ~]# rndc -c /etc/rndc.conf status
version: 9.7.0-P2-RedHat-9.7.0-21.P2.el5
CPUs found: 8
worker threads: 8
number of zones: 16
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
recursive clients: 0/0/1000
tcp clients: 0/100
server is up and running
[root@johntest ~]# rndc -c /etc/rndc.conf notify "jacktest.com"
zone notify queued
[root@johntest ~]# tail /var/log/messages
Dec 16 10:36:32 test named[10285]: received control channel command 'notify jacktest.com'
Dec 16 10:36:32 test named[10285]: zone jacktest.com/IN: sending notifies (serial 2016121404)
[root@test ~]# rndc -c /etc/rndc.conf flush[root@test ~]# rndc -c /etc/rndc.conf stop...
controls {
inet 192.168.1.3 port 953 #监听地址
allow { 192.168.1.5; } keys { "rndc-key"; }; #允许访问192.168.1.3的IP
};
[root@johntest ~]# scp /etc/rndc.conf 192.168.1.5:/root/[root@johntest ~]# vi /etc/rndc.conf #192.168.1.5从NS
# Start of rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "PElKGniJbHk/esQ9zpN+xg==";
};
options {
default-key "rndc-key";
default-server 192.168.1.3;
default-port 953;
};[root@johntest ~]# rndc -c rndc.conf status #192.168.1.5从NS,已可远程访问
version: 9.7.0-P2-RedHat-9.7.0-21.P2.el5 #一般不开放远程允许访问,非常危险
CPUs found: 8
worker threads: 8
number of zones: 16
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
recursive clients: 0/0/1000
tcp clients: 0/100
server is up and running[root@test ~]#
九、子域及子域转发(forward)forward {only|first}
forwarders {};
zone "ZONE_NAME" IN {
type forward;
forward first;
forwarders {172.168.1.3};};
新增子域服务器192.168.1.8
[root@test2 ~]# vi fin.jacktest.com.zone #192.168.1.8 子DNS
$TTL 600 ; 10 minutes
@ IN SOA ns1.fin.jacktest.com. admin.fin.jacktest.com. (
2016121701 ; serial
3600 ; refresh (1 hour)
300 ; retry (5 minutes)
172800 ; expire (2 days)
21600 ; minimum (6 hours)
)
NS ns1.fin.jacktest.com.
MX 10 mail.fin.jacktest.com.
ns1 A 192.168.1.8
mail A 192.168.1.9
www A 192.168.1.10[root@test2 ~]# service named restart
Stopping named: . [ OK ]
Starting named: [ OK ]
验证子域[root@johntest named]# dig -t A ns1.fin.jacktest.com @192.168.1.3 #通过主域可解析子域IP
; <<>> DiG 9.7.0-P2-RedHat-9.7.0-21.P2.el5 <<>> -t A ns1.fin.jacktest.com @192.168.1.3
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57664
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;ns1.fin.jacktest.com. IN A
;; ANSWER SECTION:
ns1.fin.jacktest.com. 600 IN A 192.168.1.8
;; AUTHORITY SECTION:
fin.jacktest.com. 600 IN NS ns1.fin.jacktest.com.
;; Query time: 3 msec
;; SERVER: 192.168.1.3#53(192.168.1.3)
;; WHEN: Sat Dec 17 11:11:13 2016
;; MSG SIZE rcvd: 68
[root@johntest named]# dig -t A ns1.fin.jacktest.com @192.168.1.8 #通过子域可解析子域IP
; <<>> DiG 9.7.0-P2-RedHat-9.7.0-21.P2.el5 <<>> -t A ns1.fin.jacktest.com @192.168.1.8
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 53646
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;ns1.fin.jacktest.com. IN A
;; ANSWER SECTION:
ns1.fin.jacktest.com. 600 IN A 192.168.1.8
;; AUTHORITY SECTION:
fin.jacktest.com. 600 IN NS ns1.fin.jacktest.com.
;; Query time: 2 msec
;; SERVER: 192.168.1.8#53(192.168.1.8)
;; WHEN: Sat Dec 17 11:12:39 2016
;; MSG SIZE rcvd: 68
[root@johntest named]# nslookup
> server 192.168.1.3
Default server: 192.168.1.3
Address: 192.168.1.3#53
> set q=A
> www.jacktest.com
Server: 192.168.1.3 #通过服务器192.168.1.3查找
Address: 192.168.1.3#53
Name: www.jacktest.com #查找出两条记录
Address: 192.168.1.3
Name: www.jacktest.com
Address: 192.168.1.5
> set q=A
> www.fin.jacktest.com
Server: 192.168.1.3 #通过此服务器查找
Address: 192.168.1.3#53
Non-authoritative answer: #查找出一条记录,有为非官方记录 Name: www.fin.jacktest.com
Address: 192.168.1.10
> server 192.168.1.8
Default server: 192.168.1.8
Address: 192.168.1.8#53
> set q=A
> www.fin.jacktest.com
Server: 192.168.1.8 #通过服务器192.168.1.8查找
Address: 192.168.1.8#53
Name: www.fin.jacktest.com #查找出一条记录
Address: 192.168.1.10
> set q=A
> www.jacktest.com #通过子域服务器192.168.1.8查找父域的A记录
Server: 192.168.1.8
Address: 192.168.1.8#53
** server can't find www.jacktest.com.localdomain: SERVFAIL #子域无法查找父域的A记录
>
默认子域无法查找父域信息,定义转发即可告诉子域[root@jacktest2 ~]# vi /etc/rndc.conf #192.168.1.8 子DNS 中新增以下部分
zone "jacktest.com" IN {
type forward;
forward first;
forwarders { 192.168.1.3; };
};验证:
[root@test named]# nslookup> set q=A
> www.jacktest.com
Server: 192.168.1.8 #通过服务器192.168.1.8查找
Address: 192.168.1.8#53
Non-authoritative answer:
Name: www.jacktest.com#新增forward后查找出两条记录
Address: 192.168.1.5
Name: www.jacktest.com
Address: 192.168.1.3
DNS服务器的软件bind:berkeley internet name domain
named-checkconf:检查配置文件是否有语法错误命令
named-checkzone:检查区域文件是否有语法错误命令
dig:domain information groper
dig -t NS . 查找根域的所有DNS服务器
bind97:
/etc/named.conf 主配置文件
BIND进程的工作属性
区域的定义
/etc/rndc.key
rndc: Remote Name Domain Controller
密钥文件
配置信息:/etc/rndc.conf
/var/named/ 区域数据文件
/etc/rc.d/init.d/named {start|stop|restart|status|reload}
二进制程序:named
bind-chroot:
默认:named
用户:named
组:named
/var/named/chroot/
etc/named.conf
etc/rdnc.key
sbin/named
var/named/
[root@test ~]# yum list all |grep bind
This system is not registered with RHN.
RHN support will be disabled.
bind-libs.i386 30:9.3.6-4.P1.el5 installed
bind-utils.i386 30:9.3.6-4.P1.el5 installed
[root@test ~]# rpm -e bind-libs bind-utils #rpm -e 卸载软件包
[root@test ~]# yum list all |grep bind
This system is not registered with RHN.
RHN support will be disabled.
bind.i386 30:9.3.6-4.P1.el5 Media
bind-chroot.i386 30:9.3.6-4.P1.el5 Media
实验环境:CentOS6.5
一、bind安装
bind98下载地址:http://mirrors.ctyun.cn/centos/5/os/i386/CentOS/[root@johntest ~]# rpm -ivh bind97-libs-9.8.0-21.P2.el5.i386.rpm
warning: bind98-libs-9.8.0-21.P2.el5.i386.rpm: Header V3 DSA signature: NOKEY, key ID e8562897
Preparing... ################################### [100%]
1:bind98-libs ################################# [100%][root@johntest ~]# bind98-utils-9.8.0-21.P2.el5.i386.rpm
warning: bind98-utils-9.8.0-21.P2.el5.i386.rpm: Header V3 DSA signature: NOKEY, key ID e8562897
Preparing... ############################## [100%]
1:bind98-utils ############################ [100%]
[root@johntest ~]# rpm -ivh bind98-9.8.0-21.P2.el5.x86_64.rpm
warning: bind98-9.8.0-21.P2.el5.x86_64.rpm: Header V3 DSA signature: NOKEY, key ID e8562897
Preparing... ########################################### [100%]
1:bind97 ########################################### [100%]
二、编辑DNS主配置文件:
vim /etc/named.conf修改主配置文件,如下图:修改三个红色地方,保存退出

接着修改named.rfc1912.zones文件,vim /etc/named.rfc1912.zones,如下图:

三、添加设置DNS正向解析 修改zone配置文件,正向解析:[root@xuelinux etc]#cd /var/named/[root@xuelinux etc]#cp named.localhost xuelinux.cn.zone #复制并改名修改里面的内容[root@xuelinux etc]#vim xuelinux.cn.zone #("xuelinux.cn.zone"名称要和主配置文件[/etc/named.rfc1912.zones]里面定义的zone文件名一致)

5、修改zone配置文件,反向解析:[root@xuelinux etc]#cd /var/named/[root@xuelinux named]#cp named.localhost 1.168.192.zone[root@xuelinux named]#vim 1.168.192.zone(1.168.192.zone名称要和主配置[/etc/named.rfc1912.zones]文件里面定义的zone文件名一致)

6、更改防火墙设置和selinux设置[root@xuelinux named]#getenforce #查看selinux是否开启setenforce 0[root@xuelinux named]#vi /etc/sysconfig/iptables #配置防火墙端口-AINPUT -m state --state NEW -m tcp -p tcp --dport 53 -j ACCEPT-AINPUT -m state --state NEW -m udp -p udp --dport 53 -j ACCEPT-AINPUT -m state --state NEW -m tcp -p tcp --dport 953 -j ACCEPT[root@xuelinux named]#service iptables restart #重启防火墙,使规则生效
7、启动DNS服(注意DNS服务名称在linux是叫做bind)[root@xuelinux named]#service named start #启动DNS服务

8、测试检测域信息是否正常(重要)检查之前先看下 配置文件有没有读取权限 ll /var/named (如果没有读取权限, chmod +r /var/named/* 即可)

9、检查bind文件配置过程中容易出错以下命令用以检查bind配置文件及zone文件语法是否错误[root@xuelinux named]#named-checkconf /etc/named.conf[root@xuelinux named]#named-checkzone xuelinux.cn /var/named/ xuelinux.cn.zone
10、启动重启DNS服务,查看服务状态[root@xuelinux named]#service named restart[root@xuelinux named]#service network restart
测试:
通过其他PC用户端测试解析,通过nslookup进行测试,
登录到192.168.1.10客户端进行如下测试:


五、更改配制文件后即可限定查询段[root@xuelinux etc]# vi named.conf
options {
directory "/var/named"; allow-recursion { 192.168.1.0/24; }; //只允许此IP段递归查询
};zone "." IN {
type hint;
file "named.ca";
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-transfer { none; }; //none不允许所有客户端发出传送请求
};
zone "0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-transfer { none; };
};
zone "jacktest.com" IN {
type master;
file "jacktest.com.zone";
allow-transfer { 192.168.1.5; }; //只允许此IP发出传送请求
};
zone "1.168.192.in-addr.arpa" IN {
type master;
file "192.168.1.zone";
allow-transfer { 192.168.1.5; };
};[root@johntest etc]# tail /var/log/messagesDec 15 14:11:41 test named[7276]: zone 1.168.192.in-addr.arpa/IN: loaded serial 2016121401
Dec 15 14:11:41 test named[7276]: zone jacktest.com/IN: loaded serial 20161214
Dec 15 14:11:41 test named[7276]: zone localhost/IN: loaded serial 0
Dec 15 14:11:41 test named[7276]: running
Dec 15 14:13:31 test named[7276]: client 192.168.1.5#58423: transfer of 'jacktest.com/IN': AXFR started
Dec 15 14:13:31 test named[7276]: client 192.168.1.5#58423: transfer of 'jacktest.com/IN': AXFR ended
六、设置从DNS服务器
[root@jacktest named]# setenforce 0
setenforce: SELinux is disabled[root@jacktest named]# scp 192.168.1.3:/etc/named.conf /etc/
The authenticity of host '192.168.1.3 (192.168.1.3)' can't be established.
RSA key fingerprint is c2:f2:75:5c:ab:4a:43:d3:e1:76:bc:d2:0f:c7:d6:32.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.1.3' (RSA) to the list of known hosts.
root@192.168.1.3's password:
named.conf
[root@johntest etc]# vi /etc/named.conf...
zone "jacktest.com" IN {
type slave;
file "slaves/jacktest.com.zone";
allow-transfer { 192.168.1.5; };
};
zone "1.168.192.in-addr.arpa" IN {
type slave;
file "slaves/192.168.1.zone";
allow-transfer { 192.168.1.5; };
};验证:
[root@johntest slaves]# tail /var/log/messages #192.168.1.3主
Dec 15 15:43:35 test named[7595]: zone 1.168.192.in-addr.arpa/IN: loaded serial 2016121401
Dec 15 15:43:35 test named[7595]: zone jacktest.com/IN: loaded serial 20161214
Dec 15 15:43:35 test named[7595]: zone localhost/IN: loaded serial 0
Dec 15 15:43:35 test named[7595]: running
Dec 15 15:44:12 test named[7595]: client 192.168.1.5#47432: transfer of 'jacktest.com/IN': AXFR started
Dec 15 15:44:12 test named[7595]: client 192.168.1.5#47432: transfer of 'jacktest.com/IN': AXFR ended
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#34268: transfer of 'jacktest.com/IN': AXFR started
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#34268: transfer of 'jacktest.com/IN': AXFR ended
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#59389: transfer of '1.168.192.in-addr.arpa/IN': AXFR started #传送开始
Dec 15 17:25:29 test named[7595]: client 192.168.1.5#59389: transfer of '1.168.192.in-addr.arpa/IN': AXFR ended #传送结果[root@johntest named]# tail /var/log/messages #192.168.1.5
Dec 15 17:28:13 jacktest named[10089]: zone localhost/IN: loaded serial 0
Dec 15 17:28:13 jacktest named[10089]: running
Dec 15 17:28:13 jacktest named[10089]: zone jacktest.com/IN: Transfer started.
Dec 15 17:28:13 jacktest named[10089]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: connected using 192.168.1.5#34268
Dec 15 17:28:13 jacktest named[10089]: zone jacktest.com/IN: transferred serial 20161214
Dec 15 17:28:13 jacktest named[10089]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: Transfer completed: 1 messages, 9 records, 233 bytes, 0.004 secs (58250 bytes/sec)
Dec 15 17:28:13 jacktest named[10089]: zone 1.168.192.in-addr.arpa/IN: Transfer started.
Dec 15 17:28:13 jacktest named[10089]: transfer of '1.168.192.in-addr.arpa/IN' from 192.168.1.3#53: connected using 192.168.1.5#59389
Dec 15 17:28:13 jacktest named[10089]: zone 1.168.192.in-addr.arpa/IN: transferred serial 2016121401
Dec 15 17:28:13 jacktest named[10089]: transfer of '1.168.192.in-addr.arpa/IN' from 192.168.1.3#53: Transfer completed: 1 messages, 7 records, 219 bytes, 0.002 secs (109500 bytes/sec)
七、测试NS自动更新到从服务器
[root@johntest named]# vi jacktest.com.zone #192.168.1.3主
$TTL 600
jacktest.com. IN SOA ns1.jacktest.com. admin.jacktest.com. (
2016121404 #3改成4
...
imap IN A 192.168.1.6haha IN A 192.168.1.7 #新增一条记录
[root@test named]# service named reload
Reloading named: [ OK ]
[root@johntest named]# tail /var/log/messages #192.168.1.3主NS
Dec 16 10:05:53 test named[10112]: reloading configuration succeeded
Dec 16 10:05:53 test named[10112]: reloading zones succeeded
Dec 16 10:05:53 test named[10112]: zone jacktest.com/IN: loaded serial 2016121404
Dec 16 10:05:53 test named[10112]: zone jacktest.com/IN: sending notifies (serial 2016121404)
Dec 16 10:05:53 test named[10112]: client 192.168.1.5#50038: transfer of 'jacktest.com/IN': AXFR-style IXFR started
Dec 16 10:05:53 test named[10112]: client 192.168.1.5#50038: transfer of 'jacktest.com/IN': AXFR-style IXFR ended
[root@johntest named]# tail /var/log/messages #192.168.1.5从NS
Dec 16 10:08:38 jacktest named[12536]: client 192.168.1.3#6791: received notify for zone 'jacktest.com'
Dec 16 10:08:38 jacktest named[12536]: zone jacktest.com/IN: Transfer started.
Dec 16 10:08:38 jacktest named[12536]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: connected using 192.168.1.5#50038
Dec 16 10:08:38 jacktest named[12536]: zone jacktest.com/IN: transferred serial 2016121404
Dec 16 10:08:38 jacktest named[12536]: transfer of 'jacktest.com/IN' from 192.168.1.3#53: Transfer completed: 1 messages, 13 records, 309 bytes, 0.002 secs (154500 bytes/sec)
Dec 16 10:08:38 jacktest named[12536]: zone jacktest.com/IN: sending notifies (serial 2016121404)[root@johntest slaves]# cat jacktest.com.zone #192.168.1.5从NS
jacktest.com IN SOA ns1.jacktest.com. admin.jacktest.com. (
2016121404 ; serial
...
ftp CNAME www
haha A 192.168.1.7 #自动学习成功
八、开放[b]远程访问DC[/b]Remote Name Daemon Control # [di:mn]守护进程
[root@johntest ~]# rndc-confgen > /etc/rndc.conf
[root@johntest ~]# cat /etc/rndc.conf
# Start of rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "PElKGniJbHk/esQ9zpN+xg==";
};
options {
default-key "rndc-key";
default-server 127.0.0.1;
default-port 953;
};
# End of rndc.conf
# Use with the following in named.conf, adjusting the allow list as needed:
# key "rndc-key" {
# algorithm hmac-md5;
# secret "PElKGniJbHk/esQ9zpN+xg==";
# };
#
# controls {
# inet 127.0.0.1 port 953
# allow { 127.0.0.1; } keys { "rndc-key"; };
# };
# End of named.conf #绿色部分复制添加到named.conf
[root@johntest ~]# rndc -c /etc/rndc.conf status
rndc: connection to remote host closed
This may indicate that
* the remote server is using an older version of the command protocol,
* this host is not authorized to connect,
* the clocks are not synchronized, or
* the key is invalid.
[root@johntest ~]# rm /etc/rndc.key
rm: remove regular file `/etc/rndc.key'? y
[root@test ~]# rndc -c /etc/rndc.conf status
rndc: connection to remote host closed
This may indicate that
* the remote server is using an older version of the command protocol,
* this host is not authorized to connect,
* the clocks are not synchronized, or
* the key is invalid.
[root@test ~]# service named restart
Stopping named: . [ OK ]
Generating /etc/rndc.key: [ OK ]
Starting named: [ OK ]
[root@johntest ~]# rndc -c /etc/rndc.conf status
version: 9.7.0-P2-RedHat-9.7.0-21.P2.el5
CPUs found: 8
worker threads: 8
number of zones: 16
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
recursive clients: 0/0/1000
tcp clients: 0/100
server is up and running
[root@johntest ~]# rndc -c /etc/rndc.conf notify "jacktest.com"
zone notify queued
[root@johntest ~]# tail /var/log/messages
Dec 16 10:36:32 test named[10285]: received control channel command 'notify jacktest.com'
Dec 16 10:36:32 test named[10285]: zone jacktest.com/IN: sending notifies (serial 2016121404)
[root@test ~]# rndc -c /etc/rndc.conf flush[root@test ~]# rndc -c /etc/rndc.conf stop...
controls {
inet 192.168.1.3 port 953 #监听地址
allow { 192.168.1.5; } keys { "rndc-key"; }; #允许访问192.168.1.3的IP
};
[root@johntest ~]# scp /etc/rndc.conf 192.168.1.5:/root/[root@johntest ~]# vi /etc/rndc.conf #192.168.1.5从NS
# Start of rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "PElKGniJbHk/esQ9zpN+xg==";
};
options {
default-key "rndc-key";
default-server 192.168.1.3;
default-port 953;
};[root@johntest ~]# rndc -c rndc.conf status #192.168.1.5从NS,已可远程访问
version: 9.7.0-P2-RedHat-9.7.0-21.P2.el5 #一般不开放远程允许访问,非常危险
CPUs found: 8
worker threads: 8
number of zones: 16
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
recursive clients: 0/0/1000
tcp clients: 0/100
server is up and running[root@test ~]#
九、子域及子域转发(forward)forward {only|first}
forwarders {};
zone "ZONE_NAME" IN {
type forward;
forward first;
forwarders {172.168.1.3};};
新增子域服务器192.168.1.8
[root@test2 ~]# vi fin.jacktest.com.zone #192.168.1.8 子DNS
$TTL 600 ; 10 minutes
@ IN SOA ns1.fin.jacktest.com. admin.fin.jacktest.com. (
2016121701 ; serial
3600 ; refresh (1 hour)
300 ; retry (5 minutes)
172800 ; expire (2 days)
21600 ; minimum (6 hours)
)
NS ns1.fin.jacktest.com.
MX 10 mail.fin.jacktest.com.
ns1 A 192.168.1.8
mail A 192.168.1.9
www A 192.168.1.10[root@test2 ~]# service named restart
Stopping named: . [ OK ]
Starting named: [ OK ]
验证子域[root@johntest named]# dig -t A ns1.fin.jacktest.com @192.168.1.3 #通过主域可解析子域IP
; <<>> DiG 9.7.0-P2-RedHat-9.7.0-21.P2.el5 <<>> -t A ns1.fin.jacktest.com @192.168.1.3
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57664
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;ns1.fin.jacktest.com. IN A
;; ANSWER SECTION:
ns1.fin.jacktest.com. 600 IN A 192.168.1.8
;; AUTHORITY SECTION:
fin.jacktest.com. 600 IN NS ns1.fin.jacktest.com.
;; Query time: 3 msec
;; SERVER: 192.168.1.3#53(192.168.1.3)
;; WHEN: Sat Dec 17 11:11:13 2016
;; MSG SIZE rcvd: 68
[root@johntest named]# dig -t A ns1.fin.jacktest.com @192.168.1.8 #通过子域可解析子域IP
; <<>> DiG 9.7.0-P2-RedHat-9.7.0-21.P2.el5 <<>> -t A ns1.fin.jacktest.com @192.168.1.8
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 53646
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;ns1.fin.jacktest.com. IN A
;; ANSWER SECTION:
ns1.fin.jacktest.com. 600 IN A 192.168.1.8
;; AUTHORITY SECTION:
fin.jacktest.com. 600 IN NS ns1.fin.jacktest.com.
;; Query time: 2 msec
;; SERVER: 192.168.1.8#53(192.168.1.8)
;; WHEN: Sat Dec 17 11:12:39 2016
;; MSG SIZE rcvd: 68
[root@johntest named]# nslookup
> server 192.168.1.3
Default server: 192.168.1.3
Address: 192.168.1.3#53
> set q=A
> www.jacktest.com
Server: 192.168.1.3 #通过服务器192.168.1.3查找
Address: 192.168.1.3#53
Name: www.jacktest.com #查找出两条记录
Address: 192.168.1.3
Name: www.jacktest.com
Address: 192.168.1.5
> set q=A
> www.fin.jacktest.com
Server: 192.168.1.3 #通过此服务器查找
Address: 192.168.1.3#53
Non-authoritative answer: #查找出一条记录,有为非官方记录 Name: www.fin.jacktest.com
Address: 192.168.1.10
> server 192.168.1.8
Default server: 192.168.1.8
Address: 192.168.1.8#53
> set q=A
> www.fin.jacktest.com
Server: 192.168.1.8 #通过服务器192.168.1.8查找
Address: 192.168.1.8#53
Name: www.fin.jacktest.com #查找出一条记录
Address: 192.168.1.10
> set q=A
> www.jacktest.com #通过子域服务器192.168.1.8查找父域的A记录
Server: 192.168.1.8
Address: 192.168.1.8#53
** server can't find www.jacktest.com.localdomain: SERVFAIL #子域无法查找父域的A记录
>
默认子域无法查找父域信息,定义转发即可告诉子域[root@jacktest2 ~]# vi /etc/rndc.conf #192.168.1.8 子DNS 中新增以下部分
zone "jacktest.com" IN {
type forward;
forward first;
forwarders { 192.168.1.3; };
};验证:
[root@test named]# nslookup> set q=A
> www.jacktest.com
Server: 192.168.1.8 #通过服务器192.168.1.8查找
Address: 192.168.1.8#53
Non-authoritative answer:
Name: www.jacktest.com#新增forward后查找出两条记录
Address: 192.168.1.5
Name: www.jacktest.com
Address: 192.168.1.3
相关文章推荐
- DNS域名解析之bind应用
- DNS域名解析服务(bind)
- RHEL 5服务篇—部署DNS域名解析服务(一)BIND软件
- RHEL 5服务篇—部署DNS域名解析服务(一)BIND软件
- std::bind(二)
- ButterKnife.bind(this)发生NullPointerException
- [spring security] - LDAP configuration - Bind approach
- DNS and Bind (二)
- 新手和菜鸟必须掌握的Linux命令
- 每天一个常用的linux命令(3)--mkdir
- DNS之bind,转发,子域转发,授权等配置 推荐
- Linux命令(34):ping
- jQuery的.bind()、.live()和.delegate()之间区别
- 菜鸟级别的一些最基础的linux命令实例详解
- Android Service 之三(Bind Service, 继承自 Binder 类)
- linux命令:chmod
- 常用的linux命令
- JS中的call、apply、bind方法
- Boost.bind 的使用
- redhat6.4上Cassandra 3.9节点无法加入服务器(unable to bind IP:port)问题的解决
