Linux与云计算——第二阶段Linux服务器架设 第六章:目录Directory服务器架设—FreeIPA
2016-08-01 17:20
861 查看
[b]Linux与云计算——第二阶段Linux服务器架设[/b]
第六章:目录Directory服务器架设—FreeIPA

1 FreeIPA 配置FreeIPA服务器
Configure IPA Server to share users' account in your local network.[1] Install FreeIPA.[root@dlp ~]# yum -y install ipa-server ipa-server-dns bind bind-dyndb-ldap[2] Setup FreeIPA Server.[root@dlp ~]# vi /etc/hosts# add own IP 10.0.0.30 dlp.srv.world dlp [root@dlp ~]# ipa-server-install --setup-dns The log file for this installation can be found in /var/log/ipaserver-install.log==============================================================================This program will set up the IPA Server. This includes: * Configure a stand-alone CA (dogtag) for certificate management * Configure the Network Time Daemon (ntpd) * Create and configure an instance of Directory Server * Create and configure a Kerberos Key Distribution Center (KDC) * Configure Apache (httpd) To accept the default shown in brackets, press the Enter key. # setup DNS (existing BIND settings is over-written)Existing BIND configuration detected, overwrite? [no]: yesEnter the fully qualified domain name of the computeron which you're setting up server software. Using the form<hostname>.<domainname>Example: master.example.com. # confirm the hostname and EnterServer host name [dlp.srv.world]: The domain name has been determined based on the host name. # confirm the domain name and EnterPlease confirm the domain name [srv.world]: The kerberos protocol requires a Realm name to be defined.This is typically the domain name converted to uppercase. # confirm realm name and EnterPlease provide a realm name [SRV.WORLD]:Certain directory server operations require an administrative user.This user is referred to as the Directory Manager and has full accessto the Directory for system management tasks and will be added to theinstance of directory server created for IPA.The password must be at least 8 characters long. # Directory Manager's passwordDirectory Manager password:Password (confirm): The IPA server requires an administrative user, named 'admin'.This user is a regular system account used for IPA server administration. # IPA admin's passwordIPA admin password:Password (confirm): # answer with yes or no for setting DNS forwarderDo you want to configure DNS forwarders? [yes]:Enter the IP address of DNS forwarder to use, or press Enter to finish.# specify DNS forwarder's IP if you set DNS forwarderEnter IP address for a DNS forwarder: 10.0.0.10DNS forwarder 10.0.0.10 added# Enter with empty if DNS forwarder is OKEnter IP address for a DNS forwarder:# answer with yes or no for setting reverse zoneDo you want to configure the reverse zone? [yes]:# reverse zone name if you set reverse zonePlease specify the reverse zone name [0.0.10.in-addr.arpa.]: The IPA Master Server will be configured with:Hostname: dlp.srv.worldIP address: 10.0.0.30Domain name: srv.worldRealm name: SRV.WORLD BIND DNS server will be configured to serve IPA domain with:Forwarders: 10.0.0.10Reverse zone: 0.0.10.in-addr.arpa. # confirm settings and proceed with "yes"Continue to configure the system with these values? [no]: yes The following operations may take some minutes to complete.Please wait until the prompt is returned. Configuring NTP daemon (ntpd).........==============================================================================Setup complete Next steps: 1. You must make sure these network ports are open: TCP Ports: * 80, 443: HTTP/HTTPS * 389, 636: LDAP/LDAPS * 88, 464: kerberos UDP Ports: * 88, 464: kerberos * 123: ntp 2. You can now obtain a kerberos ticket using the command: 'kinit admin' This ticket will allow you to use the IPA tools (e.g., ipa user-add) and the web user interface. Be sure to back up the CA certificate stored in /root/cacert.p12This file is required to create replicas. The password for thisfile is the Directory Manager password[3] Get Kerberos tickets and change default shell.[root@dlp ~]# kinit admin Password for admin@SRV.WORLD:# IPA admin password[root@dlp ~]# klist # confirmTicket cache: KEYRING:persistent:0:0Default principal: admin@SRV.WORLD Valid starting Expires Service principal03/21/2015 14:25:53 03/24/2015 14:25:50 krbtgt/SRV.WORLD@SRV.WORLD [root@dlp ~]# ipa config-mod --defaultshell=/bin/bash Maximum username length: 32 Home directory base: /home Default shell: /bin/bash Default users group: ipausers Default e-mail domain: srv.world Search time limit: 2 Search size limit: 100 User search fields: uid,givenname,sn,telephonenumber,ou,title Group search fields: cn,description Enable migration mode: FALSE Certificate Subject base: O=SRV.WORLD Password Expiration Notification (days): 4 Password plugin features: AllowNThash SELinux user map order: guest_u:s0$xguest_u:s0$user_u:s0$staff_u:s0-s0:c0.c1023$unconfined_u:s0-s0:c0.c1023 Default SELinux user: unconfined_u:s0-s0:c0.c1023 Default PAC types: MS-PAC[4] If Firewalld is running, allow FreeIPA services.[root@dlp ~]# firewall-cmd --add-service={ssh,dns,freeipa-ldap,freeipa-ldaps} --permanent success[root@dlp ~]# firewall-cmd --reload Success2 增加用户账户
Add User Accounts on FreeIPA Server.[1] Add a user. The password set on here is required to change at initial login.[root@dlp ~]# ipa user-add cent --first=CentOS --last=Linux --password Password:# set passwordEnter Password again to verify:-----------------Added user "cent"----------------- User login: cent First name: CentOS Last name: Linux Full name: CentOS Linux Display name: CentOS Linux Initials: CL Home directory: /home/cent GECOS field: CentOS Linux Login shell: /bin/bash Kerberos principal: cent@SRV.WORLD Email address: cent@srv.world UID: 1219600001 GID: 1219600001 Password: True Kerberos keys available: True # confirm[root@dlp ~]# ipa user-find cent --------------1 user matched-------------- User login: cent First name: CentOS Last name: Linux Home directory: /home/cent Login shell: /bin/bash Email address: cent@srv.world UID: 1219600001 GID: 1219600001 Account disabled: False Password: True Kerberos keys available: True----------------------------Number of entries returned 1[2] Add Existing local Users to IPA Directory ( set the same password with the username on this example, but it is required to change at initial login )[root@dlp ~]# vi ipauser.sh# extract local users who have 1000-9999 digit UID# this is an example#!/bin/bash for line in `grep "x:[1-9][0-9][0-9][0-9]:" /etc/passwd`do USER=`echo $line | cut -d: -f1` FIRST=`echo $line | cut -d: -f5 | awk {'print $1'}` LAST=`echo $line | cut -d: -f5 | awk {'print $2'}` [ ! "$FIRST" ] && FIRST=$USER [ ! "$LAST" ] && LAST=$USER echo $USER | ipa user-add $USER --first=$FIRST --last=$LAST --passworddone[root@dlp ~]# sh ipauser.sh -------------------Added user "redhat"------------------- User login: redhat First name: redhat Last name: redhat Full name: redhat redhat Display name: redhat redhat Initials: rr Home directory: /home/redhat GECOS field: redhat redhat Login shell: /bin/bash Kerberos principal: redhat@SRV.WORLD Email address: redhat@srv.world UID: 1219600003 GID: 1219600003 Password: True Kerberos keys available: True-------------------Added user "ubuntu"------------------- User login: ubuntu First name: ubuntu Last name: ubuntu Full name: ubuntu ubuntu Display name: ubuntu ubuntu Initials: uu Home directory: /home/ubuntu GECOS field: ubuntu ubuntu Login shell: /bin/bash Kerberos principal: ubuntu@SRV.WORLD Email address: ubuntu@srv.world UID: 1219600004 GID: 1219600004 Password: True Kerberos keys available: True3 配置FreeIPA客户端
Configure FreeIPA Client to connect to FreeIPA Server.[1] Add DNS entry for FreeIPA client on FreeIPA server first.# ipa dnsrecord-add [domain name] [record name] [record type] [record][root@dlp ~]# ipa dnsrecord-add srv.world client01 --a-rec 10.0.0.51 Record name: client01 A record: 10.0.0.51[2] Install Client tools on FreeIPA Client Host and change DNS settings.[root@client01 ~]# yum -y install ipa-client[root@client01 ~]# nmcli c modify eno16777736 ipv4.dns 10.0.0.30 [root@client01 ~]# nmcli c down eno16777736; nmcli c up eno16777736[3] Setup as a FreeIPA Client. Sync time with FreeIPA server before it.[root@client01 ~]# ipa-client-install Discovery was successful!Hostname: client01.srv.worldRealm: SRV.WORLDDNS Domain: srv.worldIPA Server: dlp.srv.worldBaseDN: dc=srv,dc=world # confirm settings and proceed with "yes"Continue to configure the system with these values? [no]: yes# answer with adminUser authorized to enroll computers: adminSynchronizing time with KDC...Unable to sync time with IPA NTP server, assuming the time is in sync. Please check that 123 UDP port is opened.Password for admin@SRV.WORLD:Successfully retrieved CA cert Subject: CN=Certificate Authority,O=SRV.WORLD Issuer: CN=Certificate Authority,O=SRV.WORLD Valid From: Fri Mar 20 01:42:15 2015 UTC Valid Until: Tue Mar 20 01:42:15 2035 UTC Enrolled in IPA realm SRV.WORLD..........Configured /etc/ssh/ssh_configConfigured /etc/ssh/sshd_configClient configuration complete. # configure mkhomedir if you need ( homedirs of users are created at inital login )[root@client01 ~]# authconfig --enablemkhomedir --update getsebool: SELinux is disabled[root@client01 ~]# exit logoutCentOS Linux 7 (Core)Kernel 3.10.0-123.20.1.el7.x86_64 on an x86_64client01 login: redhat # IPA userPassword: # passwordPassword expired. Change your password now. # required to change the password when initial loginCurrent Password: # current passwordNew password: # new passwordRetype new password:Creating home directory for redhat.[redhat@client01 ~]$ # just logined4 基础配置
[1] Add a FreeIPA user account.[root@dlp ~]# ipa user-add cent --first=CentOS --last=Linux --password Password:Enter Password again to verify:-----------------Added user "cent"----------------- User login: cent First name: CentOS Last name: Linux Full name: CentOS Linux Display name: CentOS Linux Initials: CL Home directory: /home/cent GECOS field: CentOS Linux Login shell: /bin/bash Kerberos principal: cent@SRV.WORLD Email address: cent@srv.world UID: 1781800001 GID: 1781800001 Password: True Kerberos keys available: True[2] Lock or unlock a FreeIPA user.[root@dlp ~]# ipa user-disable cent ----------------------------Disabled user account "cent"----------------------------[root@dlp ~]# ipa user-enable cent ---------------------------Enabled user account "cent"---------------------------[3] Search a FreeIPA user.[root@dlp ~]# ipa user-find cent --------------1 user matched-------------- User login: cent First name: CentOS Last name: Linux Home directory: /home/cent Login shell: /bin/bash Email address: cent@srv.world UID: 1781800001 GID: 1781800001 Account disabled: False Password: True Kerberos keys available: True----------------------------Number of entries returned 1---------------------------- [root@dlp ~]# ipa user-show --raw cent uid: cent givenname: CentOS sn: Linux homedirectory: /home/cent loginshell: /bin/bash mail: cent@srv.world uidnumber: 1781800001 gidnumber: 1781800001 nsaccountlock: False has_password: True has_keytab: True[4] Delete a FreeIPA user.[root@dlp ~]# ipa user-del cent -------------------Deleted user "cent"-------------------[5] Add a FreeIPA group.[root@dlp ~]# ipa group-add --desc='Development Group' development -------------------------Added group "development"------------------------- Group name: development Description: Development Group GID: 1781800006[6] Add members in a FreeIPA group.[root@dlp ~]# ipa group-add-member --users=redhat,ubuntu development Group name: development Description: Development Group GID: 1781800006 Member users: redhat, ubuntu-------------------------Number of members added 2-------------------------[7] Add a group in a FreeIPA group.[root@dlp ~]# ipa group-add-member --groups=development hiroshima Group name: hiroshima Description: State Group GID: 1781800007 Member groups: development-------------------------Number of members added 1-------------------------[8] Search a FreeIPA group.[root@dlp ~]# ipa group-find development ---------------1 group matched--------------- Group name: development Description: Development Group GID: 1781800006 Member users: redhat, ubuntu Member of groups: hiroshima----------------------------Number of entries returned 1----------------------------[9] Delete a FreeIPA group.[root@dlp ~]# ipa group-del hiroshima -------------------------Deleted group "hiroshima"-------------------------5 使用WEB图形化界面
It's possible to operate FreeIPA Server on Web Management Console.[1] Start Web browser on any Client on the same network of FreeIPA Server and access to "https://(FreeIPA server's hostname or IP address)/", then, login form to IPA server is shown like follows. Login with a FreeIPA user. This example use admin user like follows.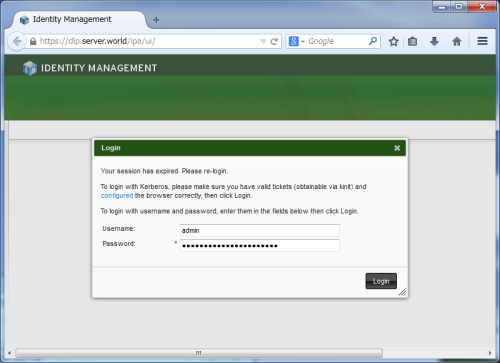
[2] Just logined noramlly. It's possible to operate FreeIPA server on GUI easily.
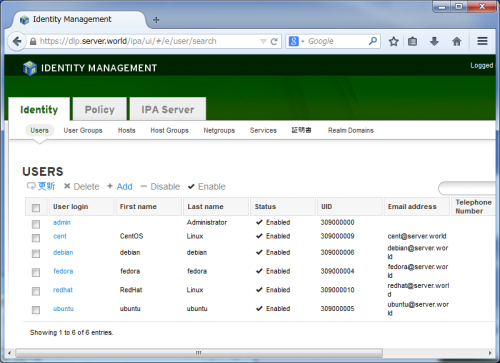
6 FreeIPA ReplicationConfigure FreeIPA Replication.[1] Install FreeIPA server's tools on the Replica Host and change DNS settings.[root@repl01 ~]# yum -y install ipa-server ipa-server-dns bind bind-dyndb-ldap# change DNS to FreeIPA server[root@repl01 ~]# nmcli c modify eno16777736 ipv4.dns 10.0.0.30 [root@repl01 ~]# nmcli c down eno16777736; nmcli c up eno16777736[2] Add DNS entry for Replica Host on FreeIPA server.# ipa dnsrecord-add [domain name] [record name] [record type] [record][root@dlp ~]# ipa dnsrecord-add srv.world repl01 --a-rec 10.0.0.61 Record name: repl01 A record: 10.0.0.61 [root@dlp ~]# ipa-replica-prepare repl01.srv.world --ip-address 10.0.0.61 Directory Manager (existing master) password: # Directory Manager password Preparing replica for repl01.srv.world from dlp.srv.worldCreating SSL certificate for the Directory ServerCreating SSL certificate for the dogtag Directory ServerCreating SSL certificate for the Web ServerExporting RA certificateCopying additional filesFinalizing configurationPackaging replica information into /var/lib/ipa/replica-info-repl01.srv.world.gpgAdding DNS records for repl01.srv.worldUsing reverse zone 0.0.10.in-addr.arpa. # transfer generated key to Replica Host[root@dlp ~]# scp /var/lib/ipa/replica-info-repl01.srv.world.gpg root@repl01.srv.world:/var/lib/ipa/ root@repl01.srv.world's password:replica-info-repl01.srv.world.gpg 100% 35KB 34.6KB/s 00:00[3] On FreeIPA server, If Firewalld is running, allow FreeIPA replication service.[root@dlp ~]# firewall-cmd --add-service=freeipa-replication --permanent success[root@dlp ~]# firewall-cmd --reload Success[4] On FreeIPA replication Host, If Firewalld is running, allow FreeIPA services.[root@repl01 ~]# firewall-cmd --add-service={ssh,dns,freeipa-ldap,freeipa-ldaps,freeipa-replication} --permanent success[root@repl01 ~]# firewall-cmd --reload Success[5] Setup as a Replica Server on FreeIPA Replica.The following example set "--no-forwarders" for DNS, but if you set it, specify like "--forwarder=x.x.x.x".[root@repl01 ~]# ipa-replica-install --setup-ca --setup-dns --no-forwarders /var/lib/ipa/replica-info-repl01.srv.world.gpg Directory Manager (existing master) password: # Directory Manager password Run connection check to masterCheck connection from replica to remote master 'dlp.srv.world': Directory Service: Unsecure port (389): OK Directory Service: Secure port (636): OK Kerberos KDC: TCP (88): OK Kerberos Kpasswd: TCP (464): OK HTTP Server: Unsecure port (80): OK HTTP Server: Secure port (443): OK PKI-CA: Directory Service port (7389): OK The following list of ports use UDP protocol and would need to bechecked manually: Kerberos KDC: UDP (88): SKIPPED Kerberos Kpasswd: UDP (464): SKIPPED Connection from replica to master is OK.Start listening on required ports for remote master checkGet credentials to log in to remote masteradmin@SRV.WORLD password: # admin password Execute check on remote master..........Global DNS configuration in LDAP server is emptyYou can use 'dnsconfig-mod' command to set global DNS options thatwould override settings in local named.conf files Restarting the web server[6] Get Kerberos tickets on Replica Host and make sure it's possible to get datas on FreeIPA Directory. If possible, it's OK to setup replication settings. For FreeIPA Clients, it's not necessarry to set additinal settings, Clients can continue to authenticate even if a Server is down.[root@repl01 ~]# kinit admin Password for admin@SRV.WORLD: # admin password[root@repl01 ~]# klist Ticket cache: KEYRING:persistent:0:0Default principal: admin@SRV.WORLD Valid starting Expires Service principal03/21/2015 15:13:38 03/24/2015 15:13:35 krbtgt/SRV.WORLD@SRV.WORLD [root@repl01 ~]# ipa user-find ---------------4 users matched--------------- User login: admin Last name: Administrator Home directory: /home/admin Login shell: /bin/bash UID: 1219600000 GID: 1219600000 Account disabled: False Password: True Kerberos keys available: True User login: cent First name: CentOS Last name: Linux Home directory: /home/cent Login shell: /bin/bash Email address: cent@srv.world UID: 1219600001 GID: 1219600001 Account disabled: False Password: True Kerberos keys available: True..........
详细视频课程请戳—→ http://edu.51cto.com/course/course_id-6574.html
相关文章推荐
- Linux与云计算——第二阶段Linux服务器架设 第六章:目录Directory服务器架设—OpenLDAP
- Linux与云计算——第二阶段Linux服务器架设 第六章:目录Directory服务器架设—NIS
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—用户目录虚拟主机和SSL
- Linux与云计算——第二阶段 第一十一章:代理Proxy服务器架设—Squid配置反向代理
- Linux与云计算——第二阶段 第四章:DNS服务器架设4-启用密钥加密传输
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—Nginx(上)
- Linux与云计算——第二阶段 第五章:存储Storage服务器架设—分布式存储GlusterFS基础
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—使用各种WEB脚本环境
- Linux与云计算——第二阶段 第四章:DNS服务器架设2-正向反向解析的正向反向解析
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—日志分析平台
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—代理模块
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—认证
- Linux与云计算——第二阶段Linux服务器架设 第一十二章:数据库搭建—MariaDB
- Linux与云计算——第二阶段Linux服务器架设 第八章:FTP服务器架设—安装配置FTP服务和客户端配置
- Linux与云计算——第二阶段 第十章:Samba服务器架设—SMB共享目录及多用户SMB挂载
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—wiki系统Mediawiki
- Linux与云计算——第二阶段Linux服务器架设 第一十二章:数据库搭建—PostgreSQL
- Linux与云计算——第二阶段 第四章:DNS服务器架设3-部署从服务器
- Linux与云计算——第二阶段Linux服务器架设 第七章:网站WEB服务器架设—WEB基础
- Linux与云计算——第二阶段Linux服务器架设 第八章:FTP服务器架设—vsftpd 使用 TLS/SSL
