物联网与嵌入式系统概论-week4-Networking and the Internet-Lesson2: Internet Protocol
2015-11-20 23:38
615 查看
This series of articles are the study notes of "An Introduction
to Programming the Internet of Things", by Prof. Harris, Department of Computer Science, University of California, Irvine. This article is week 4, Lessen 2: Internet Protocols.
We don't want to go into detail in protocols. But you have to know they exist because the hardware that we buy when we make our IoT device, the hardware that we buy, we'll buy it matching a particular protocol.
So we'll pick the protocol and pick the hardware to match that. So we need to know at least the existence of protocols and what they are.
Can be changed by anyone at any time
Internet structure is ad hoc, that is, it's very irregular. People can join the network, leave the network. I can open up a laptop in this room right now and suddenly it will be part of the internet,
and people can send messagesto it. And then if I shut it off, it is now temporarily no longer part of the network. So, the internet is very dynamic. It has an unpredictable structure, but it still has to work. Actually, it's pretty amazing that it works as
well as it does, given the fact that it's so crazy. So it can be changed by anyone at any time,so you have to be able to send messages between this wide variety of network types.
consistently send messages regardless of everything else.
rules, hopefully a minimal set of rules, which as long as everybody adheres to those rules. Everybody can communicate. And you want to make these rules minimal so that they're not a burden on the local area network.
Protocol software running on each host androuter
Common communication rules for all networks
So the internet has protocols associated with it, which if you want to talk on the internet, your networks have to support these protocols.
Now just to give you some intuition about what a protocol is, it's basically something that you add. It usually involves adding data to a method. Regular type of data to a message.
And then when they're done they just say over and out. So this is aprotocol.
But you get the idea. A protocol is basically extra data that you add, is represented by extra data you add to the message, like the word over or the word over and out. Right. There all kinds of
rules that extra data that you put in there that are used to enable communication. So we call those, that a protocol,that's a set of rules that enables communication which minimally constrains the message. It adds a little
bit of data to the message typically. That's what a protocol is.
using the internet, if you want your machine to talk on the internet, they have to use Internet Protocol. They have to adhere to the rules of IP. Now TCP is another protocol and that protocol is, it also is used in conjunction
with the internet. So if you use the internet you're either using TCP or UDP. And you're using IP. So I said TCP/IP it could also be UDP/IP. You put those together and that's internet. So you can do anything else you want,
you can add all kinds of other data into the message. As long as you adhere to those protocols, you can talk on the internet and your machines can communicate with other machines on the internet.
inside these protocols and what they define.
Internet has to have an IP address, and so each host and router gets assigned at least one of the seInternet addresses. Now when you say least one, basically it should be one to every network adapter.
Each host (and router) is assigned at least one of these unique internet ddress
Internet protocol, one very important thing it does is it gives this naming scheme, this unique naming scheme. Every machine on the Internet has to have a different name. And now there are problems
with this, right, because IP addresses are not that long. IP addresses are four byte numbers, four single bytes, so you've seen them referred to as these, let's see like 124.254.27.33. OK, and they're four numbers sepparated by dots. So it's four numbers and
each number can range from 0 to 255. So there aren't that many addresses compared to how many network components there are these day, because of IOT. There's so many things on a network. You need so many addresses. So there are a lot of challenges in dealing
with that.
define a packet, a chunk of data, and it's gotta be sent from machine to machine to machine because these machines are not directly wired together. They're not within radio range directly. There has to be a route taken, so it has to hop from one machine to
the next. So these protocols define methods of doing routing. Of how you send a message through a sequence of machines to get to the destination you want go to, that's one important
role.
header. So, payload is the actual data that you want to send.
The header is the information that is sort of metadata. It's about the packet, but it's not the actual payload of the packet, not the important part of the packet. It's not the data you want to send. But it
has information about the packet. Now generally the header information comesfrom the network protocols. So the data in the network protocol, that the network protocol uses, it gets put into the header, typically.
message you say over. And that word over is actually added to theend of the message. We call that footer because it’s at the end. Header and footer is the same thing that add at the beginning and or the end of the payload.
CBradio protocol – footer
“over” – I am done talking
“Roger” – Data received
Text that you put, something that you add to the beginning you'd call header. And header and footer are the same thing added at the beginning or added at the end. Excess overhead
data is required to help you adhere to the protocol but it’s not the actual data that you want to send. So, these rules enable efficient communication. These rules, these header and footer rules, the data you put in them,
you need that so that at the receiving end you know like, for instance, with CB, you know oh, I heard the word, over. That means I can talk now. So, in order to establish efficient communication, you need that information that's containedin the header and
footer. And, for instance, with routing and the Internet, some of that information inside the header will be important for routing.
So, all the different functions that the seprotocols handle, they use information inside the header typically to do that. There are many different tasks that are performed by protocols, by network
protocols. But some of those are routing, you know, figuring out a route sequence of machines to send a packet through to get to its destination.
Flow control
Flow control making sure that you don't have a bottleneck. That all of your traffic isn't going through one router. That you spread it out over different routers so that you can get good traffic
flow.
Arbitration
Arbitration means when you have some kindof a network segment where only one packet can travel at a time and two packets want to travel. So say two machines want to send messages on this one piece
of network segment at the same time. Then, somehow you have to arbitrate. You have to figure out which one gets to go first. So, there are rules for all these things, and all these rules are encoded inside the network
protocols. So, the protocols define those rules. What do you do when two machines want to talk on the same wire at the same time. The set of rules, that's called network protocol. All these protocols are very complicatedin
general. And because they are so complicated, what people have done, is they've divided the protocols into layers.
is one layer. Flow control is another layer. Arbitration is maybe another layer. It just separates them. Now, all these layers have to be taken care of, but the separation is generally good for coding frankly. Because
writing one piece of code that handles all those complex tasks at once, it would be one nasty piece of code. So it makes a lot of sense to cut that code up, to separate the responsibilities across different layers, and then
write different pieces of code for each layer. And then let the different layers of code work together. So that's what the OSI model does. It proposes a set of layers.
Now the Internet uses a similar set of layers, maybe a more compressed version of that, but definitely the idea of taking all these complicated tasks and dividing them amongst different layers of protocolsis
a good thing to reduce the complexity and make the coding more manageable. So each layer has it's own responsibilities, and each layer uses different data.
(4) Each layer uses different data
Routing requires network topology
Arbitration may use message priorities
that in practice certainly in this specialization, in practice you're not going to be writing aprotocol stack, making a protocol stack, but you can use a protocol stack. So you at least would want to know what this term is because it gets thrown around. If
you want to make a new embedded system you say, well I need to be networked, you know Internet, which protocol stack am I going to use. Which implementation of the protocol stack will I use? You need to know what that term
means, because it getsused a lot when you're actually coding things. You should know basically what it means.
to handle.
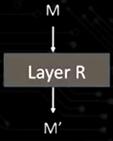
Massage M is received by layer R
M is our message, and that's maybe just the payload okay. That is what the data we want to send. So then that is basically an input to a layer. Let's talk about the first layer, layer R let's say is the first
layer.
Layer R identifies a route for message M’
So
M goes into the code, so that code takes the message, it makes some kind of adecision, whatever decisions are made at that layer, and then it puts the results of that decision into the header of the message producing a new message,
M’ down there, which is now bigger.It has whatever was inside M and it has additional header on the outside of that. So at every level that happens. let's see this level is performing routing. So the goal of this level is
to take a message and figure out a sequence of machines that it will hop through to get to its destination. So at this level it takes a message, it finds the route, it says okay you need to go through machines A, B, C, and D. So it can take a sequence, that
whole sequence of nodes, put that into the header of the message, and then output this new message, M’ which is the same old message, but now with this extra routing message contained inside the header.
Layer R passes message M’ to the next lower layer
So that's the general idea, that at every layer the code, or the hardware, or whatever it is that's implementing the protocol, will make some decisions like routing information, arbitration information, flow
control information. And then the results of that it'll put into the header, or some of the results, it'll put directly into the header, and you'll get a new message out, which is bigger than the original one. Which now has its new header data. This is on
the sending side.
So this is the idea, and you have a stack of these layers. So that's what they mean by protocol stack, you have layer after layer and they call that a stack.
is separated.
with it. So it is encapsulated, it's separating the different layers. And the whole point of that is to make it simpler to understand and also to write code.
at another layer.
A transmission, when want to send amessage, basically the messages start at the top layer and then they go down. So you put the messages into the top layer protocol. It makes its decisions, adds to the header,
and passes it to the next layer, which adds, makes some decisions, adds to the header and continues, until you get to the bottom layer.
Message decisions are made at each layer
Relevant information is added to the messageat each layer (header or footer)
Now the bottom layer is called the physicallayer, and at that layer it actually takes the data and puts it on to an electrical mechanism, a transmission mechanism, some kind of medium. So that means one of
two things, either wire, so a physical layer, it codes the data onto physical wires, or it encodes it onto wireless broadcasts, radio broadcasts, so one of the two. So always at the bottom layer there's this physical layer, which actually transmits the signal
either by wire or through the air through radio.
the messages goup through the same protocol stack. So that means when it's received, it's received at the physical layer. Because it's physical signals, either wired or wireless. They come in, and then they have
to get basically recoded back to the original data. So now at the receiving end, these messages are going through the protocol stack up, from bottom up. So the opposite of what happened on transmission happens here. At
every layer, the message gets received, the appropriate header information is read and used, and then the new message that's produced is actually smaller than the first message, minus that header information. And then it goes up to the next layer, which
takes the header information at that layer it uses that and then producesa new message which is smaller. And so by the end at the top all you have is the actual payload and all the header information has been stripped off.
So that what happens at the receiving end and it's the reverse of what happens at the transmission side.
to Programming the Internet of Things", by Prof. Harris, Department of Computer Science, University of California, Irvine. This article is week 4, Lessen 2: Internet Protocols.
2. Lecture2 Internet Protocols
2.1 Lecture 2.1 Internet Structure
So this lecture we'll talk a little bit about the internet and structure and we'll get into internet protocols. We'll talkabout whata network protocol is. We have to know a little bit about these.We don't want to go into detail in protocols. But you have to know they exist because the hardware that we buy when we make our IoT device, the hardware that we buy, we'll buy it matching a particular protocol.
So we'll pick the protocol and pick the hardware to match that. So we need to know at least the existence of protocols and what they are.
2.1.1 Internet Structure
(1) Ad hocinterconnection of networks
Unpredictable structureCan be changed by anyone at any time
Internet structure is ad hoc, that is, it's very irregular. People can join the network, leave the network. I can open up a laptop in this room right now and suddenly it will be part of the internet,
and people can send messagesto it. And then if I shut it off, it is now temporarily no longer part of the network. So, the internet is very dynamic. It has an unpredictable structure, but it still has to work. Actually, it's pretty amazing that it works as
well as it does, given the fact that it's so crazy. So it can be changed by anyone at any time,so you have to be able to send messages between this wide variety of network types.
(2) Messages travel fromsource to destination by hopping through
So you've got these LANs that maybe use different protocols, routers that are speaking different protocols, destination LAN, it speaks a different protocol. And so you've got this, you've got to be able toconsistently send messages regardless of everything else.
2.1.2 Internet Protocol Solution
Protocols are basically a set of rules, rules of communication. If we're talking about for network protocols it's a set of rules of communication. And there are a lot of rules. But generally, it's a set ofrules, hopefully a minimal set of rules, which as long as everybody adheres to those rules. Everybody can communicate. And you want to make these rules minimal so that they're not a burden on the local area network.
Protocol software running on each host androuter
Common communication rules for all networks
So the internet has protocols associated with it, which if you want to talk on the internet, your networks have to support these protocols.
Now just to give you some intuition about what a protocol is, it's basically something that you add. It usually involves adding data to a method. Regular type of data to a message.
(1) Example of a protocol of old radio communication
Protocol is something like that and they're on the radio, and they say something. Something like “over”. They say over at the end of their message. And as soon as they say over, somebody else can start talking.And then when they're done they just say over and out. So this is aprotocol.
But you get the idea. A protocol is basically extra data that you add, is represented by extra data you add to the message, like the word over or the word over and out. Right. There all kinds of
rules that extra data that you put in there that are used to enable communication. So we call those, that a protocol,that's a set of rules that enables communication which minimally constrains the message. It adds a little
bit of data to the message typically. That's what a protocol is.
(2) TCP/IP Protocol
TCP/IP is the most common set of protocols for internet. In fact specifically IP stands for Internet Protocol and if you'reusing the internet, if you want your machine to talk on the internet, they have to use Internet Protocol. They have to adhere to the rules of IP. Now TCP is another protocol and that protocol is, it also is used in conjunction
with the internet. So if you use the internet you're either using TCP or UDP. And you're using IP. So I said TCP/IP it could also be UDP/IP. You put those together and that's internet. So you can do anything else you want,
you can add all kinds of other data into the message. As long as you adhere to those protocols, you can talk on the internet and your machines can communicate with other machines on the internet.
2.2 Lecture 2.2 Protocols
So we'll talk a little bit about protocols,network protocols, Internet protocols specifically and what the irresponsibilities are. We won't go into great depth. But we want to give you a flavor of what's containedinside these protocols and what they define.
2.2.1 What does a internet protocol do?
An Internet Protocol, meaning IP or TCP or UDP, they do several things. One basic thing is provide a naming scheme. Actually that's a very important thing. Every component on theInternet has to have an IP address, and so each host and router gets assigned at least one of the seInternet addresses. Now when you say least one, basically it should be one to every network adapter.
(1) Provides anaming scheme
An internet protocol defines a uniform format of host addressesEach host (and router) is assigned at least one of these unique internet ddress
Internet protocol, one very important thing it does is it gives this naming scheme, this unique naming scheme. Every machine on the Internet has to have a different name. And now there are problems
with this, right, because IP addresses are not that long. IP addresses are four byte numbers, four single bytes, so you've seen them referred to as these, let's see like 124.254.27.33. OK, and they're four numbers sepparated by dots. So it's four numbers and
each number can range from 0 to 255. So there aren't that many addresses compared to how many network components there are these day, because of IOT. There's so many things on a network. You need so many addresses. So there are a lot of challenges in dealing
with that.
(2) Protocols provide a delivery mechanism
Also, these protocols provide a delivery mechanism. So what we mean by that is that whenever you send a message from one machine to another machine, you gotta go through a sequence of machines. You've gottadefine a packet, a chunk of data, and it's gotta be sent from machine to machine to machine because these machines are not directly wired together. They're not within radio range directly. There has to be a route taken, so it has to hop from one machine to
the next. So these protocols define methods of doing routing. Of how you send a message through a sequence of machines to get to the destination you want go to, that's one important
role.
(3) Another thing is that it defines the header
Another thing is that it defines the header. The header and the payload. So by header, if you look at any packet. You can usually break it up into header and payload, maybe footer too, but let's just talk aboutheader. So, payload is the actual data that you want to send.
The header is the information that is sort of metadata. It's about the packet, but it's not the actual payload of the packet, not the important part of the packet. It's not the data you want to send. But it
has information about the packet. Now generally the header information comesfrom the network protocols. So the data in the network protocol, that the network protocol uses, it gets put into the header, typically.
2.2.2 Protocol Model
(1) Rules that determine how computers will communicate(2) Footer
Citizen ban radio, you say over at the end of talking and roger means data received and so on. So that would be called footer. So you say a message and then at the end of yourmessage you say over. And that word over is actually added to theend of the message. We call that footer because it’s at the end. Header and footer is the same thing that add at the beginning and or the end of the payload.
CBradio protocol – footer
“over” – I am done talking
“Roger” – Data received
Text that you put, something that you add to the beginning you'd call header. And header and footer are the same thing added at the beginning or added at the end. Excess overhead
data is required to help you adhere to the protocol but it’s not the actual data that you want to send. So, these rules enable efficient communication. These rules, these header and footer rules, the data you put in them,
you need that so that at the receiving end you know like, for instance, with CB, you know oh, I heard the word, over. That means I can talk now. So, in order to establish efficient communication, you need that information that's containedin the header and
footer. And, for instance, with routing and the Internet, some of that information inside the header will be important for routing.
(3) Payload
The payload is the text. So say I say something like, hello, my name is Ian Harris, over.Hello, my name is Ian Harris, that's the actual payload.(4) Rules enable efficient communication
2.2.3 Network Protocols
(1) Many networking task to transmit and receive data
RoutingSo, all the different functions that the seprotocols handle, they use information inside the header typically to do that. There are many different tasks that are performed by protocols, by network
protocols. But some of those are routing, you know, figuring out a route sequence of machines to send a packet through to get to its destination.
Flow control
Flow control making sure that you don't have a bottleneck. That all of your traffic isn't going through one router. That you spread it out over different routers so that you can get good traffic
flow.
Arbitration
Arbitration means when you have some kindof a network segment where only one packet can travel at a time and two packets want to travel. So say two machines want to send messages on this one piece
of network segment at the same time. Then, somehow you have to arbitrate. You have to figure out which one gets to go first. So, there are rules for all these things, and all these rules are encoded inside the network
protocols. So, the protocols define those rules. What do you do when two machines want to talk on the same wire at the same time. The set of rules, that's called network protocol. All these protocols are very complicatedin
general. And because they are so complicated, what people have done, is they've divided the protocols into layers.
(2) OSI divides these tasks between network abstraction layers
So, OSI, open system interconnect model, OSI model. It presents what's called a protocol stack. Classification protocol. So it takes all the things that these network protocols do and it divides them up. So routingis one layer. Flow control is another layer. Arbitration is maybe another layer. It just separates them. Now, all these layers have to be taken care of, but the separation is generally good for coding frankly. Because
writing one piece of code that handles all those complex tasks at once, it would be one nasty piece of code. So it makes a lot of sense to cut that code up, to separate the responsibilities across different layers, and then
write different pieces of code for each layer. And then let the different layers of code work together. So that's what the OSI model does. It proposes a set of layers.
Now the Internet uses a similar set of layers, maybe a more compressed version of that, but definitely the idea of taking all these complicated tasks and dividing them amongst different layers of protocolsis
a good thing to reduce the complexity and make the coding more manageable. So each layer has it's own responsibilities, and each layer uses different data.
(3) Each layer has its own responsibilities
(4) Each layer uses different data
Routing requires network topologyArbitration may use message priorities
2.3 Lecture 2.3 Protocol Stack
This lecture we'll talk about what aprotocol stack is, really define that term. We will go into a little bit of detail, little bit of information about how a protocol stack is defined. Now remember though,that in practice certainly in this specialization, in practice you're not going to be writing aprotocol stack, making a protocol stack, but you can use a protocol stack. So you at least would want to know what this term is because it gets thrown around. If
you want to make a new embedded system you say, well I need to be networked, you know Internet, which protocol stack am I going to use. Which implementation of the protocol stack will I use? You need to know what that term
means, because it getsused a lot when you're actually coding things. You should know basically what it means.
2.3.1 OSI Layer Concept
(1) Message is received at each layer and decisions aremade
OSI Layer Concept. So the idea about taking these protocols and making a stack, different layers of protocol, is that you've got these multiple layers, different tasks, different networking tasks that you haveto handle.
(2) Assume layer R performs routing, transmission

Massage M is received by layer R
M is our message, and that's maybe just the payload okay. That is what the data we want to send. So then that is basically an input to a layer. Let's talk about the first layer, layer R let's say is the first
layer.
Layer R identifies a route for message M’
So
M goes into the code, so that code takes the message, it makes some kind of adecision, whatever decisions are made at that layer, and then it puts the results of that decision into the header of the message producing a new message,
M’ down there, which is now bigger.It has whatever was inside M and it has additional header on the outside of that. So at every level that happens. let's see this level is performing routing. So the goal of this level is
to take a message and figure out a sequence of machines that it will hop through to get to its destination. So at this level it takes a message, it finds the route, it says okay you need to go through machines A, B, C, and D. So it can take a sequence, that
whole sequence of nodes, put that into the header of the message, and then output this new message, M’ which is the same old message, but now with this extra routing message contained inside the header.
Layer R passes message M’ to the next lower layer
So that's the general idea, that at every layer the code, or the hardware, or whatever it is that's implementing the protocol, will make some decisions like routing information, arbitration information, flow
control information. And then the results of that it'll put into the header, or some of the results, it'll put directly into the header, and you'll get a new message out, which is bigger than the original one. Which now has its new header data. This is on
the sending side.
So this is the idea, and you have a stack of these layers. So that's what they mean by protocol stack, you have layer after layer and they call that a stack.
2.3.2 Encapsulation
Encapsulation is used to mean that the protocols they're separated from one another, in some sense. So, each layer, each protocol layeris separated.
(1) Communication tasks are confined to one protocol layer
So, all these different tasks that need tobe performed. Say routing, that is mapped to a particular layer. That is performed by the protocol information stack at this layer and other layers do not have to dealwith it. So it is encapsulated, it's separating the different layers. And the whole point of that is to make it simpler to understand and also to write code.
(2) Protocol stack is the implementation (usually software) of each protocol layer
All right, so as a programmer, if you're dealing with the layer that deals with routing, then that's all you have to think about, you don't have to think about flow control because flow control is dealt withat another layer.
2.3.3 Encapsulation: transmission
Messages start at top layer and go downA transmission, when want to send amessage, basically the messages start at the top layer and then they go down. So you put the messages into the top layer protocol. It makes its decisions, adds to the header,
and passes it to the next layer, which adds, makes some decisions, adds to the header and continues, until you get to the bottom layer.
Message decisions are made at each layer
Relevant information is added to the messageat each layer (header or footer)
Now the bottom layer is called the physicallayer, and at that layer it actually takes the data and puts it on to an electrical mechanism, a transmission mechanism, some kind of medium. So that means one of
two things, either wire, so a physical layer, it codes the data onto physical wires, or it encodes it onto wireless broadcasts, radio broadcasts, so one of the two. So always at the bottom layer there's this physical layer, which actually transmits the signal
either by wire or through the air through radio.
2.3.4 Encapsulation: reception
Now, at the receiving end, the message comes in. Remember, it's sent physically. So it's on wires, it's a bunch of electrical signals on wires, or it's sent through the radio. So at this end,the messages goup through the same protocol stack. So that means when it's received, it's received at the physical layer. Because it's physical signals, either wired or wireless. They come in, and then they have
to get basically recoded back to the original data. So now at the receiving end, these messages are going through the protocol stack up, from bottom up. So the opposite of what happened on transmission happens here. At
every layer, the message gets received, the appropriate header information is read and used, and then the new message that's produced is actually smaller than the first message, minus that header information. And then it goes up to the next layer, which
takes the header information at that layer it uses that and then producesa new message which is smaller. And so by the end at the top all you have is the actual payload and all the header information has been stripped off.
So that what happens at the receiving end and it's the reverse of what happens at the transmission side.
相关文章推荐
- 物联网与嵌入式系统概论-week4-Networking and the Internet-Lesson1: Networking Basics
- JerryScript 和 IoT.js:来自三星的物联网JavaScript
- 超越Web,Javascript在物联网的应用
- 哈工大物联网感知技术学习心得
- 几种物联网实现方式之间的比较+转载
- 物联网安全思考
- 物联网信息整理
- 物联网与嵌入式系统概论-week3- Hardware and Software-Lesson3: Operating Systems
- 物联网与嵌入式系统概论-week3- Hardware and Software-Lesson2: Microcontrollers and Software
- 物联网与嵌入式系统概论-week3- Hardware and Software-Lesson1: Hardware Components
- 参加Autodesk 2015 开发者大会:物联网有意思的试验
- 朱老师物联网大讲堂学习总结
- iotables 软件防火墙基础命令讲解(一)
- STL之next()函数和iota函数
- WinHec 2015 深圳秋季技术大会 Windows 10物联网+Azure云
- 国际物联网展会盛大开幕 解放号众包平台再成焦点
- HDU 4609 3-idiots(FFT学习)
- 物联网与嵌入式系统概论-week2-Embedded Systems-Lesson3: Interacting with the Physical World
- 物联网与嵌入式系统概论-week2-Embedded Systems-Lesson2: Components of Embedded Systems
- 物联网与嵌入式系统概论-week2-Embedded Systems-Lesson1: Features and Constraints
